Your IP is the unique address that identifies your router’s interface to the Internet. You need an IP so that websites and web apps have an address to reply to.
So, how to still connect to the Internet but avoid people tracking you?
The only way to remain truly anonymous online is to mask your IP behind something (or someone) else’s IP. When you use another IP (instead of your own), you add an anonymity layer.
In this post, we’ll describe the 10 ways (and beyond) to hide your identity online truly. We’ll discuss, from VPNs, proxies, TOR, decentralization projects, and other methods that may suit different purposes, like proxy chaining, combinations, obfuscated servers, NATed DHCP, etc.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents.
- How Can Someone Track Down Your IP?
- Five Popular Methods to Hide Your IP Address.
- The NATed DHCP Addresses Method (Depends on ISP).
- Four Other Methods to Hide your IP.
- Hide Your IP: Recommendations
How Can Someone Track Down Your IP?
If you are using any website, service, or app, there is a chance they have logs with your IP. But that is not all, the infrastructure where your traffic is flowing through (ISP, government firewalls, CDNs, etc), might also know where are you coming from (your home router) and where you are going to (those torrent servers).
To learn how someone can track you down with your IP, it is important to know how an IP address is allocated.
How is an IP address allocated?
The IANA (Internet Assigned Number Authority) distributes massive blocks of IPs to RIRs (Regional Internet Registries), which are the second authority of IPs in the world.
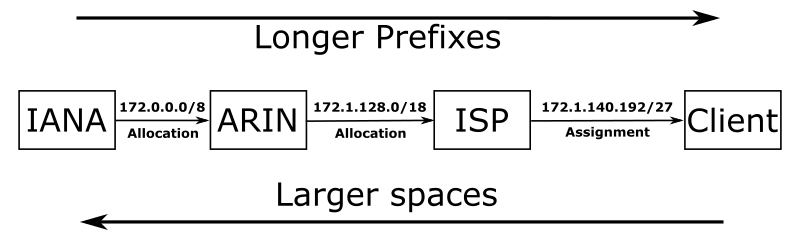
RIRs assign their IP address blocks to LIRs or ISPs (Local Internet Registries or Internet Service Providers). Finally, the LIRs of ISPs create smaller subnets and assign them per sub-region, city, or town. ISPs allocate individual (or sets) IPs to the final user or clients.
Larger spaces are regions, countries, towns. But the longer the prefix is (/32), the more specific an IP address is— the more precise the location of the device can be.
Tracing the Location of Your IP.
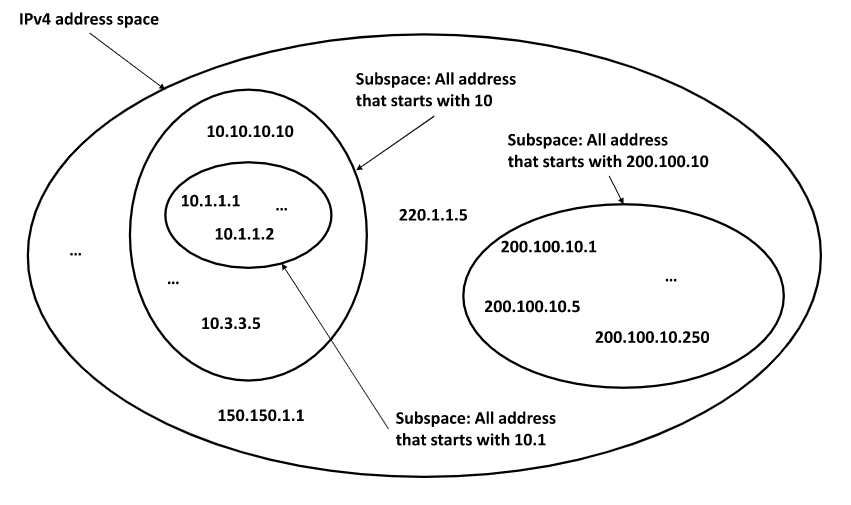
Anyone with your public IP address can use IANA’s or RIR’s databases to track you down. Anyone would be capable of tracing, first your region (RIR), and your ISP. And in some cases (with the right data in hand), your town or a wide radius of the zone.
Just like a bullseye— they’ll start from the larger scope, then begin to zoom in.
Tracing your exact home address with an IP is nearly impossible without help from the local ISP, which in many cases (except for the Five Eyes surveillance alliance) will keep your information private. In some of these countries, where data laws are strict, someone with more authority, such as a government agency could request traffic logs to an ISP. Logs might contain source IP, destination IP, protocol, application, timestamps, etc.
Logs don’t contain your home address… But your ISP’s customer database will.
IP Geolocation Services.
There are also some geolocation services that trace back public IP addresses, without the need from any ISP’s database. They do this, by identifying the RIR (your IP’s region), then zoom in as close as possible. Then use RIR databases and other wide range of data, from weather, mapping services, or basically anything where your IP is linked to a ZIP code or address. They extract data from these databases using data mining techniques.
These geolocation services can basically try to zoom in by looking for parameters associated with the IP like:
- Geographical location. Country and region.
- Country code, area code, and zip code.
- Time zone, latitude, and longitude.
- Connection speed, ISP, domain name, mobile carrier.
- Weather station name or code.
- And any detail that links your IP with a location.
A simple Google search into “What’s my IP” gave me the following information. Although I am already spoofing my geo-location, the below information is the exit node of my traffic.
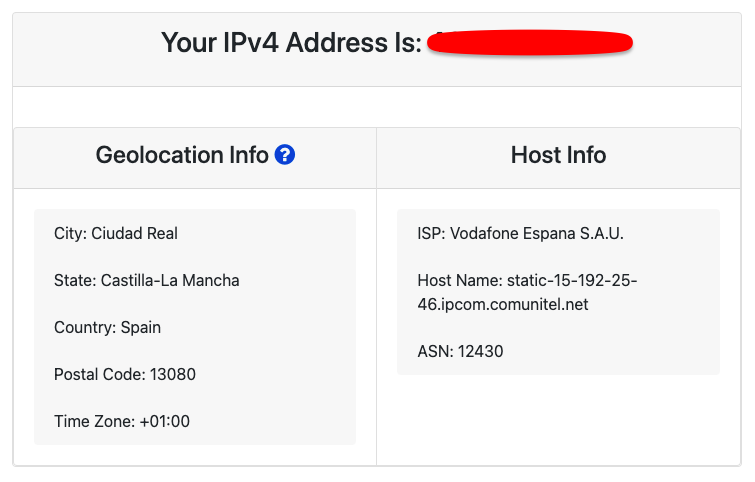
These IP geolocation services make money from websites interested in knowing where their visitors are coming from. Still, most of these IP geolocation services are not entirely precise.
Content Delivery Networks (CDNs).
Edge servers (close to the end-users) that belong to CDNs are being deployed across the world. These edge servers are helping respond to the DNS resolutions, caching streaming content, helping solve buffering, improving page load times, streaming quality, and even stopping volumetric DDoS attacks.
When CDNs have densely packed edge servers, they will help give more accurate geolocation of a visitor’s original IP. If an edge server performing a certain service is close to you, it might help capture some traffic data, such as country or area code.
Five Popular Methods to Hide Your IP Address.
To hide your IP address, all you need to do is, spoof its location!
Just like you would hire a PO Box service to redirect your mail to a third-party, other than your own home address. With your IP address, you would need to conceal it, bury it somewhere, and make it look like it is coming from somewhere else.
Although you can’t literally get away from hiding your source IP from the ISP (your Internet provider), local network, and some CDN providers, you can hide it from the destination. Plus, encrypting your data is a fantastic way to improve your anonymity level.
How to hide your IP? Use any of the following five methods below.
1. Proxy Server
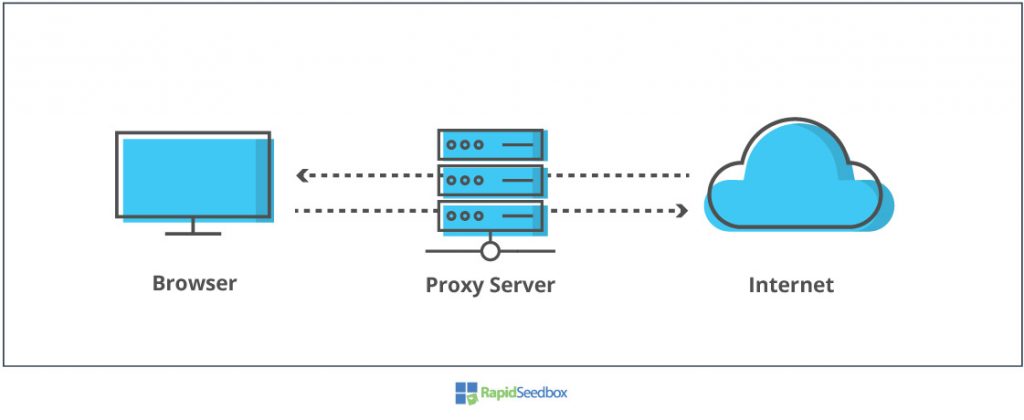
A proxy server is a middle-man, an intermediary between you and the Internet. It takes your Internet requests (HTTP, Bittorrent, FTP, etc) and changes the source IP (your identity) for its own. A proxy does not encrypt traffic as a VPN does, but it does hide your IP. There are different types of proxies; some are more anonymous and faster than others.
There is a massive difference between private and free proxies. If you are using a proxy, avoid free ones, as they put your privacy at high risk. A private proxy, on the other hand, will ensure large blocks of anonymous fresh proxies, which are perfect for hiding your IP in activities like web scraping and SEO.
Use Case: SOCKS5 proxies are suitable for torrenting and streaming. Also, use bulk proxies such as IPv6 rotating proxies (blocks of IPs) for web scraping, large-scale SEO, market research, etc.
2. Proxy Chaining.
Proxy chaining is a technique used to improve anonymity, by connecting two or more proxy servers together to forward requests to a target service or destination. When you use proxy chaining, you connect to a proxy server and then specify more proxies to use them as a chain— until you reach the destination.
Proxy Chains are fantastic mechanisms to hide your IP even deeper. When using a proxy chain, you’ll have to make sure that every proxy within the chain is operational, available, and fast. One link in the chain fails and the entire chain breaks, that is why ensuring you are using reliable and fast proxies is vital.
Use Case: It can get things a bit slower. But chaining proxies are great to double, or triple your anonymity. In fact, there is a pen test tool known as ProxyChains which forces any TCP connection made by any application to go through a series of proxies. It is popular to be used with protocols like SSH, Telnet, wget, FTP, and Nmap.
3. VPN
Virtual Private Network (VPN) is another pretty popular method for concealing an IP. It creates an encrypted tunnel between you (client) and another place on the Internet (server).
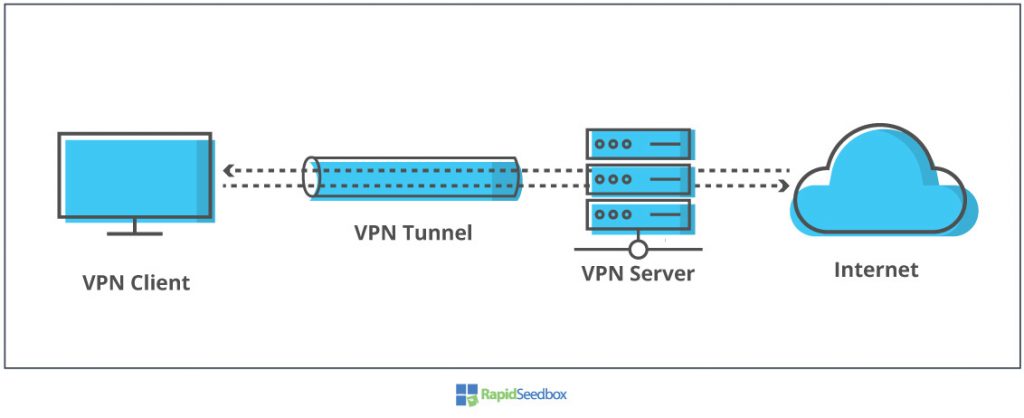
This encrypted tunnel is supported by real infrastructure, including your home router, or public Wifi access point, your local ISP, the Internet, and so on. Anyone with access to this infrastructure could intercept your traffic, but will not be able to read your data, because all traffic is encrypted. You hide your IP in the VPN server’s IP and use it as an exit node to the Internet.
The same as free proxies, stay away from free VPNs. A free VPN will likely mess with your data logs, could sell your own resources (traffic or processing power), and will show you lots of annoying ads.
Use Case: The best VPNs are right for safe browsing in public networks. Streaming and torrenting with VPNs is safer than proxies, but speed might be compromised.
4. TOR
TOR (The Onion Router) is a free and open-source project for anonymous Internet communication. It forwards your traffic across multiple hop connections using what is known as Onion routing.
To hide your IP, TOR takes your source traffic and forwards it through a worldwide, volunteer network of thousand relays. TOR also uses a client, known as “the TOR browser” to encrypt outgoing traffic,. The TOR browser connects to an entry guard which randomly takes your encrypted traffic through a series of relays, until it reaches an exit relay (closer to the destination). The exit relay unencrypts traffic and takes it to its destination.
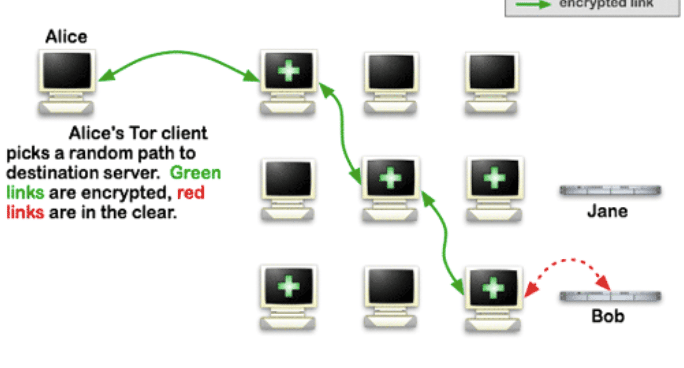
Use Case: TOR is frequently used for bypassing censorship, hiding your IP, accessing the dark web, or just if you don’t want anyone tracking your IP. TOR is not suitable for streaming or torrenting. Learn more about Tor in one of our latest posts: Is Tor Browser Safe?
5. P2P Decentralization Projects.
Peer to Peer (P2P) networks are fantastic ways to increase distribution (just like what TOR does). The projects shown below are capable of decentralizing power, which helps hide your IP deeper.
5.1. Freenet.
Freenet is based on open-source software designed to decentralized data storage and data sharing across the Internet using a P2P platform.
With Freenet, users randomly share a portion of their bandwidth and hard drive anonymously and with strong encryption. Freenet is an overlay network and is also referred to as an Internet within the Internet. Although Freenet has an amazing degree of anonymity, it has a bad reputation for its security flaws.
5.2. I2P
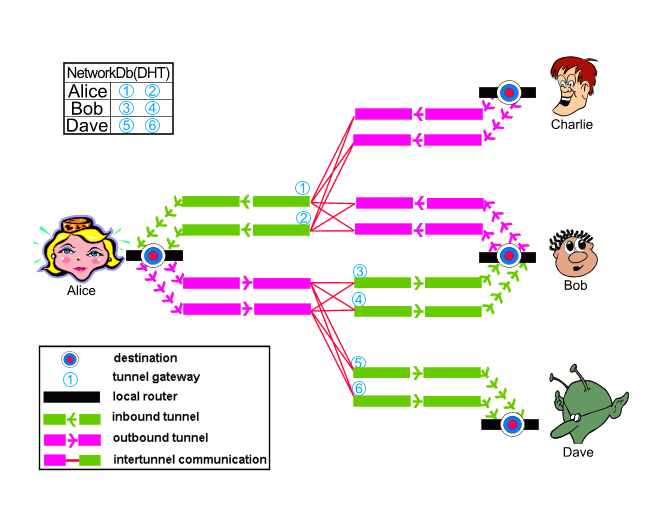
I2P (Invisible Internet Project) (a fork from Freenet), uses an anonymous P2P network, where each peer is both a client and a server. It is basically an overlay anonymity network built upon the idea of decentralization.
I2P can employ DHT and peer selection to decentralize traffic even further. I2P uses Garlic Routing (an improvement over Onion routing), which introduces caching, mixing, and encryption. Additionally, I2P uses a series of out-proxies as exit nodes to the Internet.
I2P has evolved over the years. It has hidden users from surveillance and monitoring and has been a way to access the dark web.
5.3. ZeroNet
An open and distributed P2P hosting (website) that uses Bitcoin cryptography and P2P networks. ZeroNet also leverages P2P to introduce decentralization, but it is designed for P2P hosting. ZeroNet does not relay your traffic to any central server, instead, it uses the network of peers.
The NATed DHCP Addresses Method (Depends on ISP).
ISPs are starting to have very limited public IPv4 addressing scope, so their IP address assignment policies are changing. Some ISPs might still be assigning static public IPs to home users with certain technologies like DSL, or ADSL, however, due to IPv4 exhaustion and RIR’s policies, most ISPs are starting to assign IPs dynamically.
What are NATed DHCP addresses? And why does it matter to your anonymity?
ISPs in countries from Asia, Europe, or places where IPv4 is running out, are beginning to map a single public (global) IPv4 address with many local (private) IPv4 addresses. In most cases, ISPs (especially mobile carriers) use a CGNAT (Carrier Grade NAT) to connect an entire area to the Internet using a single public IP, behind a NAT. ISPs can do this, because the network between CPEs (Customer Premises Equipment) and the ISP’s core network is, most of the time owned by ISPs.
The CGNAT will dynamically map an unused IPv4 address (Port-based) from the NAT pool to a user requesting an IP via DHCP. What this means is that when subscribers are not active, ISPs could easily re-assign those IPs.
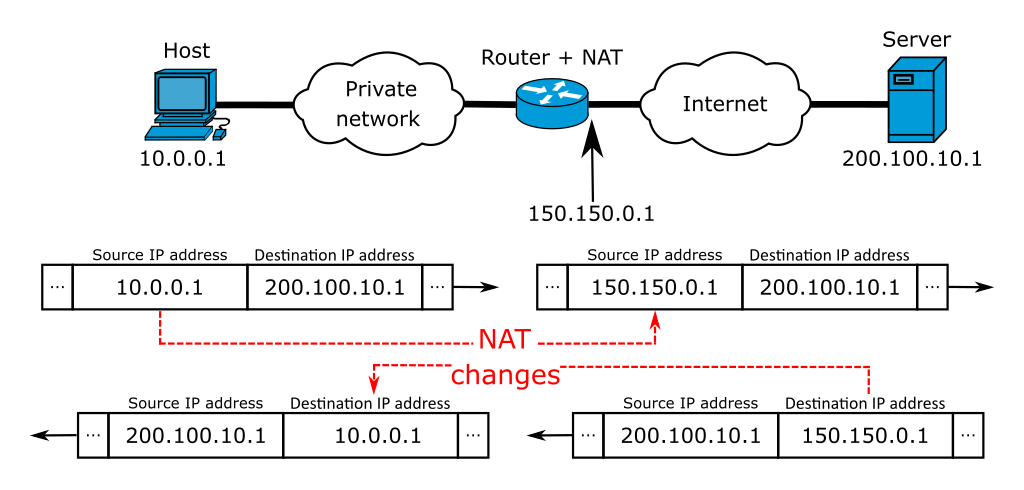
From the point of view of federal agencies, geolocation services, or copyright trolls, there are disadvantages.
- The end-to-end traceability breaks down at the CGNAT. So nobody, except your ISP could be able to trace you back.
- Most ISPs are required (depending on Federal laws) to log the mappings between private to public.
- When private IPs are dynamically assigned, they will change from user to user from time to time. So it is very challenging to trace end-users unless ISPs have a sophisticated logging system.
A way to solve this is to start the migration to IPv6, but this will take a long time.
How to hide your IP if you are getting dynamic IPs?
If you believe you are behind a CGNAT— your gateway’s WAN IP is different from your public IP (WhatsMyIP)— you can get a new IP address every time, doing the following:
- Running a simple “ipconfig /release” will renew the IP address.
- Or reboot your router.
- To avoid being easily identified within the private network, mask your MAC address or MSISDN (if you are using a mobile).
Four Other Methods to Hide Your IP.
If none of the methods shown before work for you, or you need to hide your IP differently, don’t worry there are also other ways to hide your IP.
1. Use Another IP.
When you connect to a coffee shop’s WiFi or Airport WiFi, you’ll use their IP and not yours. But bear in mind, that a big percentage of public networks are highly controlled. They might be using a proxy to control the usage of the Internet or some kind of portal with authentication and logging. Never use public networks for sensitive data, like banking or shopping, unless you use it with strong encryption (VPN or TOR).
2. OBFU Servers.
Server obfuscation (OBFU) is a process that takes data and runs a special algorithm to make it look like regular Internet activity. Obfuscated servers work as proxies that take the traffic coming from (VPNs or TOR) and make them look like regular HTTPS traffic in order to bypass firewall rules. For example, an obfuscated VPN server will hide the fact that it is using VPN protocols to forward traffic. OBFU servers are used in heavily restricted environments such as China.
3. A Seedbox.
A seedbox is a high-bandwidth remote server built and designed explicitly to download and upload files from a P2P network while hiding your source IP. You connect to a seedbox server via remote desktop or any other method and download/upload torrents to the server (and not directly to your computer) and then use safe transfer mechanisms like SFTP to transfer to your computer. With a Seedbox, your real IP is not shown in the torrent swarm, only the seedboxes.
4. Use Combinations to Hide your IP.
The more combinations you use, the deeper your online anonymity gets buried. Bear in mind that chaining privacy methods will double your privacy but will also make things much slower. A few popular examples of these combinations:
- Chaining a SOCKS5 Proxy with VPN.
- VPN over TOR or (TOR over VPN)
- Double VPN encryption.
- TOR over a Proxy (or Proxy over TOR).
Hide your IP: Recomendations
Hiding your IP address will help you improve your security and privacy while roaming the Internet. But it will also help you avoid getting your source private IP blocked, plus you’ll be able to freely unblock geo-restricted content, use P2P without worrying, bypass any network restrictions or censorship.
So, you might be unsure which path to take. Start by clearly defining your requirements. Why do you want to hide your IP? And from what?
- Safe browsing? If you want a simple “safe browsing” the TOR browser or an anonymity proxy can be perfect for that,
- Traveling too much? Abroad and need to deal with sensitive data? a VPN is the master in concealing data.
- Need automation, speed, and anonymity at the same time? IPv6 rotating proxies are the best choice. They are fresh, fast, and un-expensive.
- Need to unblock geo restricted content? VPNs and SOCKS5 proxies are perfect for the job.
0Comments