Despite being formulated over two decades ago, IPv6 adoption has some way to go. Google statistics show that as of 2024, IPv6 adoption stands at less than 45%. Part of that is due to the complexity of IPv6 migration.
If you haven’t yet begun your IPv6 migration journey – wait. It’s vital to ensure you’re adequately prepared so the “little things” don’t catch you off-guard during the process.

Table of Contents
- IPv6 Address Planning
- Hardware Compatibility Check
- Software and Application Readiness
- Security Policy Update
- IT Staff Training
- Testing and Validation
- Coexistence Strategies
- Vendor Support Assurance
- Regulatory Compliance
- Financial Planning
- Final Thoughts
Note: Before you begin, you should have foundational knowledge about IPv6. We highly recommend reading our essential guide on “What is IPv6?“
1. IPv6 Address Planning
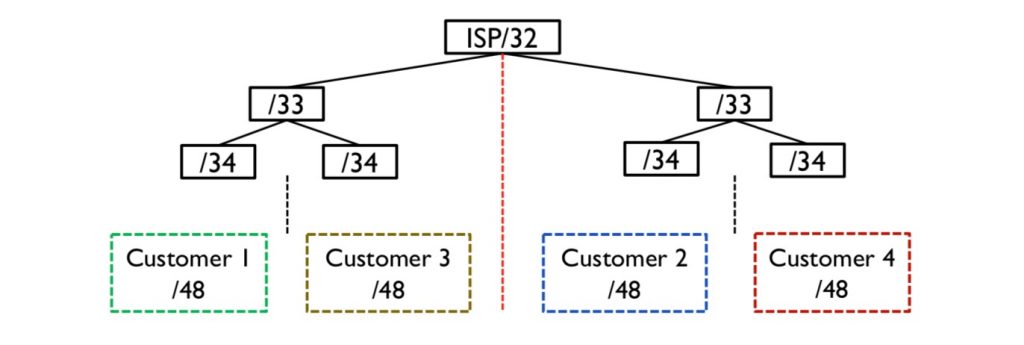
Address planning is foundational to a successful IPv6 migration. Unlike the limited and highly structured IPv4 space, IPv6 offers a virtually limitless pool of IP addresses. This abundance allows for more flexible and hierarchical address allocation.
You must devise a strategy that accounts for the size and structure of your networks. That includes considerations for global unicast addresses, subnetting practices, and the allocation of addresses for different network segments.
Recommended reading: Learn more about IPv6 Address Types.
Example
An organization might allocate a /48 prefix for each geographical site, ensuring ample address space for future growth. Within each site, individual subnets can be assigned a /64 prefix, following best practices for subnetting in IPv6.
2. Hardware Compatibility Check
Many older network devices, such as routers, switches, and firewalls, may not support IPv6 natively or may require firmware updates to do so. Conducting a thorough inventory and compatibility assessment of existing hardware is essential.
This step determines whether the equipment can be upgraded or needs replacing, impacting budget and timelines. Ensuring all hardware components are IPv6-ready avoids potential bottlenecks and compatibility issues.
Example
Before deployment, an IT team checks their existing routers, such as the Cisco Catalyst 9300 Series, against Cisco’s official documentation. This is to confirm IPv6 support and any necessary firmware upgrades.
3. Software and Application Readiness
As networks transition to IPv6, software applications must be evaluated for compatibility. This includes operating systems, management tools, and end-user applications. Many software solutions may require updates or patches to function correctly in an IPv6 environment.
You should work closely with vendors to understand software readiness and plan for necessary upgrades. This ensures critical applications remain available and performant, maintaining business continuity throughout the migration process.
Example
A company updates its DNS management software to ensure it can handle AAAA records. These are essential for mapping hostnames to IPv6 addresses. This might involve upgrading to a newer software version or patching the existing installation.
4. Security Policy Update
IPv6’s architecture includes built-in security features, such as mandatory support for IPsec. However, it also presents new challenges. One example is the complexity of IPv6 addresses, which leads to possibly overlooked security configurations.
It is essential to update security policies to address these changes. That means incorporating IPv6-specific threat models, firewall rules, and intrusion detection/prevention strategies. Only if correctly configured will you benefit from the protocol’s features for enhanced security.
Example
Transitioning to IPv6 requires updating firewall rules to match the expanded address space and new types of traffic. This might involve creating IPv6-specific rules such as ICMPv6 and neighbor discovery.
5. IT Staff Training
The successful deployment of IPv6 relies heavily on the IT staff’s knowledge and expertise. Proper skills are required to handle the deployment, management, and troubleshooting of IPv6 networks.
Training programs should cover IPv6’s technical nuances, including:
- Addressing
- Subnetting
- Configuration
- Security best practices
This investment in training is crucial for minimizing deployment errors, speeding up the migration process, and ensuring the long-term maintainability of the IPv6 infrastructure.
Example
An organization might enroll its network engineers in IPv6 training courses offered by recognized providers like Cisco or Juniper. These courses cover IPv6 fundamentals, deployment strategies, and advanced routing techniques.
6. Testing and Validation
Before full deployment, IPv6 implementations should be rigorously tested in a controlled environment. This phase allows IT teams to validate the configuration, performance, and compatibility of IPv6 with existing systems and applications.
Testing strategies might include:
- Simulating real-world traffic patterns.
- Ensuring that security measures are effective.
- Verifying that critical services are accessible via IPv6.
Through comprehensive testing, organizations can identify and resolve issues early, reducing the risk of disruptions during the wider rollout.
Example
Before a full rollout, a company sets up a test environment that mirrors its production network. This allows for the deployment and testing of IPv6 configurations on a network segment, enabling the identification and resolution of issues without impacting critical services.
7. Coexistence Strategies
Given the ongoing presence of IPv4, planning for IPv6/IPv4 coexistence is essential. Dual-stack technologies, where devices run IPv4 and IPv6, are commonly used during IPv6 transitional periods.
Alternatively, tunneling methods can encapsulate IPv6 traffic within IPv4 packets, and translation mechanisms can facilitate communication between IPv4 and IPv6 networks.
Selecting the right coexistence strategy depends on the organization’s specific needs and the expected duration of the transition period. Effective coexistence planning ensures uninterrupted service and connectivity for users and systems during the migration.
Example
Implementing dual-stack technology allows network devices to run IPv4 and IPv6 simultaneously. This approach facilitates a smooth transition by maintaining service availability across both protocols during migration.
8. Vendor Support Assurance
It’s vital to ensure that all network-related products, from infrastructure hardware to management software, are fully compatible with IPv6.
This may involve:
- Liaising with vendors to confirm support.
- Understanding potential limitations.
- Securing necessary updates or patches.
Vendor engagement also helps access technical support and guidance during the migration process. Ensuring comprehensive vendor support simplifies the transition. After all, these vendors have the expertise to address complex IPv6 deployment challenges.
Example
Before migration, a business confirms that its cloud service provider, such as AWS, supports IPv6 across its services. This includes checking for IPv6-enabled services like Amazon EC2 and Amazon VPC.
9. Regulatory Compliance
Some sectors may have specific guidelines for IPv6 deployment, including privacy, data protection, and interoperability standards. You must understand these requirements to ensure your IPv6 implementation meets regulatory obligations.
Addressing compliance from the outset of the migration project helps avoid legal and operational risks, ensuring the organization’s IPv6 network meets all necessary standards.
Example
A multinational corporation ensures its IPv6 deployment complies with the General Data Protection Regulation (GDPR). This can be done by implementing IPv6 security measures that protect personal data during transmission.
10. Financial Planning
The transition to IPv6 can have significant financial implications. Costs may include hardware and software upgrades, staff training, and potential downtime during migration. Because of this, you must develop a comprehensive budget.
The financial planning process will also help you balance the need for investment against the benefits of IPv6. Planning should also consider the long-term savings and performance improvements associated with IPv6.
Example
An organization assesses the cost implications of migrating to IPv6. These include the potential need for hardware upgrades, software licenses, staff training, and the operational impact of the transition.
11. Final Thoughts
Migrating to IPv6 is a complex but essential process that positions you for future growth. However, as you can see from the factors we’ve covered, there are ample considerations even before commencing IPv6 migration.
Knowing these factors can help you balance the right transition point for your business. Since we’re already near the halfway mark globally, you must migrate as soon as it’s financially viable.
Meanwhile, work towards the process using the factors we’ve provided so you’ll be well-equipped to move when the time comes.
RapidSeedbox offers IPv4 and IPv6 rental services. You get:
Flexibility for deployment on any server.
Direct IP acquisition – no brokers involved.
Always-available customer support.
0Comments