Although P2P file transfer, or torrenting as we know it, has been popular since the early 2000s, the media streaming revolution of the past decade has renewed its popularity. According to Ipoque’s study in 2009, 40 to 70% of internet traffic is because of P2P file transfers and these numbers have only swelled in recent times.
For starters, torrenting uses the BitTorrent protocol, where users can download and upload files. Using the BitTorrent protocol, the user need not access or download files from the central server. Instead, the user can perform those activities through other user devices.
To access BitTorrent, the user must have access to the BitTorrent client through which the P2P (peer-to-peer) file sharing is done.
Today, many BitTorrent clients are available on the internet, and if you’re aware of torrenting, you must have heard about qBittorrent and the need for using a VPN while torrenting.
Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents
- What is qBittorrent, and is it legal?
- Why is a qBittorrent VPN essential?
- Why NordVPN for qBittorrent?
- How to Set Up NordVPN for qBittorrent?
- Using NordVPN’s P2P servers.
- Using SOCKS5 proxy on qBittorrent.
- How to Verify if NordVPN is Connected with qBittorrent?
- Conclusion
1. What is qBittorrent, and is it Legal?
For starters, qBittorrent is an open-source BitTorrent client written in native C++. This project focuses on providing the user with a better experience while torrenting than the most prominent µTorrent.
The qBittorrent uses and Qt toolkit and libtorrent-rasterbar library for the backend. In addition, the new versions now feature a Python-based search engine, which serves a great purpose in searching torrents with ease.
As a generic user, one would prefer using qBittorrent as it offers more features, and the best part is that it comes with a refined user interface without ads. In addition, several tests have also claimed qBittorrent to be more reliable and quicker with downloads.
Usually, people might worry about using qBittorrent, considering it might be illegal. In reality, it is entirely legal, and surprisingly, torrenting is also legal until you download unsanctioned copyrighted material and get caught.
Read More: Is qBittorrent Safe and Reliable?
As unsanctioned copyrighted material is available for the user to download on the web, an estimate of 250 billion and above loss is estimated annually, according to the study made by Freakonomics.
2. Why is a qBittorrent VPN Essential?
Torrenting comes with many risks, and one must be aware of the dangers to prevent oneself from being a victim. Here are some cases where VPN helps enhance the user’s torrenting experience through the qBittorrent.
a. Reduces the risk of Malicious Torrent Links:
Malware-hidden torrenting links commonly affect users while they use qBittorrent. Torrent links associated with trackers, malware, and viruses are extremely dangerous compared to those on the web.
If these dangers affect the user, there is a high chance of losing all sensitive information. In the worst-case scenario, every digital device of the user linked with a joint account might be vulnerable to these dangers.
b. Anonymity from Governments and Tracking Organizations:
Some countries impose warnings and strict fines for using BitTorrent. Considering a substantial annual loss due to free access to copyrighted content, several governments and media houses have enforced internet censorship on torrent websites and search engines.
If authorities find the user downloading copyrighted content, they can hold the user guilty of committing copyright violations. For instance, if authorities catch you uploading torrents in Japan, you can land in jail for ten years.
c. Bypass ISP Throttling:
The ISP can track your online activity and throttle internet connection speeds if found using BitTorrent. To prevent these from happening, a conscious torrent user would use the VPN services, and here comes the requirement for qBittorrent VPN.
These are some of the main advantages of using the VPN while torrenting, but finding a VPN that is efficient and effective on qBittorrent is a bit harder than anticipated. It is because most VPNs on the internet are incompatible with BitTorrent clients.
After checking and testing the most prominent VPNs compatible with the BitTorrent clients, we have selected NordVPN qBittorrent as the best VPN for qBittorrent.
3. Why NordVPN for qBittorrent?
NordVPN is arguably the most effective qBittorrent VPN, as developers specially designed it with BitTorrent clients and the dangers of torrenting in mind.
NordVPN’s 5500+ stable high-speed servers and security features following the latest encryption techniques make it the best VPN for qBittorrent. The main reason for choosing NordVPN is because it supports P2P file-sharing, and the servers can handle the P2P traffic quite efficiently.
According to Sandvine’s study, people are not making P2P transfers openly. Instead, they use VPNs to obfuscate the P2P traffic for anonymity and increased speed.
Here are some of the best features of NordVPN on offer, which made us consider it the best qBittorrent VPN.
a. Auto-connection support:
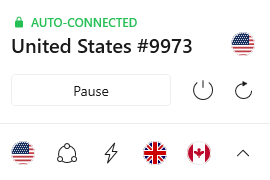
This feature comes in handy when the user forgets to turn on the VPN while torrenting, as it automatically turns on by connecting to a server.
For this feature to work correctly, the user must ensure that NordVPN isn’t disabled in the startup settings and set the priority to high.
b. Support for IP Masking and dedicated IP:
NordVPN’s IP Masking and dedicated features help the user to stay anonymous on the web. While torrenting, these features come in handy as the VPN masks the user’s PC’s public IP and replaces it with the IP assigned by the VPN.
By doing so, the trackers cannot track down the user as the IP is not visible, resulting in anonymity and enhanced privacy.
c. Offers P2P servers:
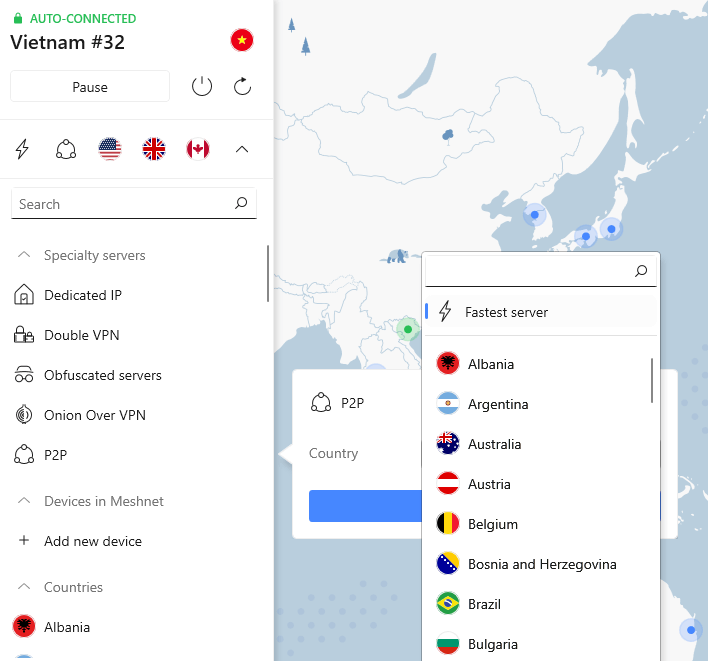
NordVPN designed its P2P servers to upload and download large torrent files through their optimized servers. NordVPN’s P2P servers allow users to download torrents very quickly, as there are no bandwidth restrictions.
Because users utilize these servers for torrenting, NordVPN provides encryption to prevent ISPs and governments from tracking the user’s activity.
d. Supports SOCKS5 Proxy:
VPNs usually associate with SOCKS5 Proxy to spoof the location by hiding the user’s IP address online. This location spoofing works by routing all the internet traffic, and just before reaching the destination, the proxy provider replaces the IP with a random IP address.
The SOCKS5 Proxy is comparatively better than the standard proxies as it provides enhanced anonymity and security to the user.
e. Features DNS Leak protection and an Internet kill switch:
DNS Leak protection makes the user aware of any DNS leaks to prevent the user’s activity from being visible to the ISP. You can recognize a DNS leak if the DNS queries travel to the ISP’s DNS servers instead of the VPN’s DNS servers.
With these DNS queries visible to the user, the ISP can analyze them and track down user activity, resulting in throttling or warnings.
On the other hand, the internet kill switch is a reliable feature, as it disconnects the connection instantly if there is any instability with the VPN connection.
f. Strict no-log policy:
The user logs are gathered by the ISPs for extended periods and sold to miners. As many users use VPNs for personal needs, one might be worried about the data being analyzed and gathered.
To put the user at peace, NordVPN offers a no-log policy where no activity is collected or analyzed without the user’s consent.
g. Advanced encryption techniques for Torrenting:
NordVPN’s encryption is achieved by passing the packets through an encrypted tunnel, which scrambles the data and makes it extremely difficult for third parties to understand and analyze it.
To achieve encryption, NordVPN uses IKEv2/IPsec, OpenVPN, and NordLynx VPN protocols, which involve AES with 256-bit keys and many other encryption algorithms.
h. NordVPN’s Threat Protection feature:
NordVPN’s CyberSec feature is updated and enhanced to create an improvised anti-malware tool called Threat Protection. This feature provides the user safety and security against most cyber threats, such as malware and ad trackers, in real time without connecting to any servers.
In addition, all the intrusive ads displayed on the web pages are blocked to prevent users from accidentally accessing malicious websites and becoming victims of trackers and malware.
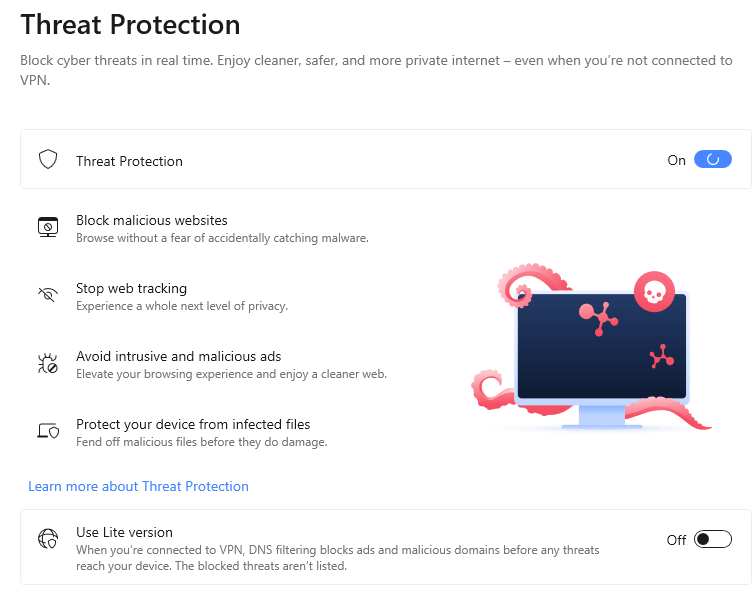
The Threat Protection feature also comes in handy when the user attempts to download a file online as they are scanned for malware thoroughly during and after downloading.
Using qBittorrent with NordVPN?
Enhance your torrenting setup with RapidSeedbox’s high-speed seedboxes. Enjoy faster downloads, improved security, and seamless integration, ensuring a smooth and efficient torrenting experience with qBittorrent.
4. How to Set Up NordVPN for qBittorrent?
Setting up qBittorrent VPN with the help of NordVPN qBittorent involves two methods. One among them doesn’t require any learning curve and is easy to implement. On the other hand, the second method consists of a series of steps that must be carefully implemented to achieve the NordVPN qBittorrent connection.
Here are the two methods to set up NordVPN for qBittorrent:
- Using NordVPN’s P2P servers.
- Using SOCKS5 proxy on qBittorrent.
a. Using NordVPN’s P2P servers:
This approach is the easiest, as the user needs to follow a series of steps to connect to NordVPN’s P2P servers for torrenting. Here are the detailed steps to set up NordVPN qBittorent through the P2P servers.
- Purchase a NordVPN subscription.
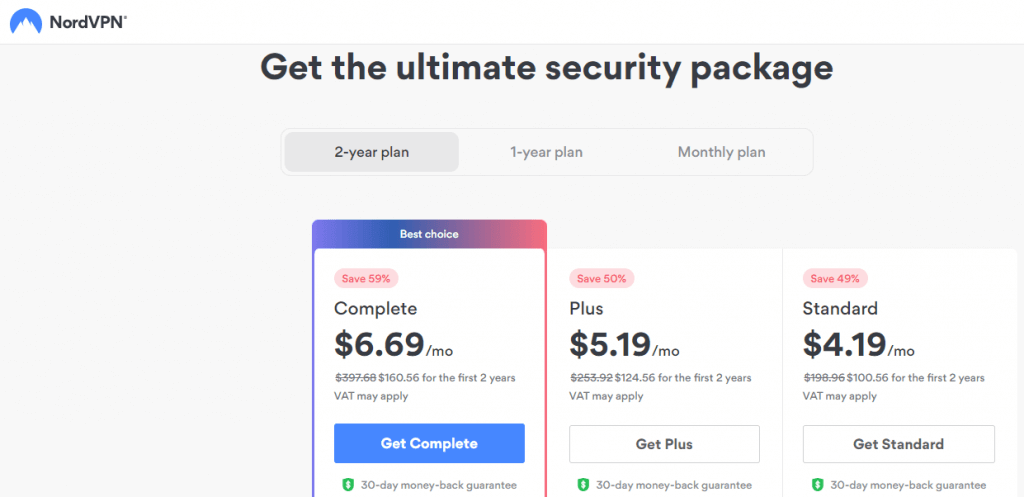
NordVPN offers flexible plans for its users and provides a detailed comparison of features that are being offered. Currently, the plans are available in monthly and yearly packages, along with a 30-day trial pack.
- Select the P2P server.
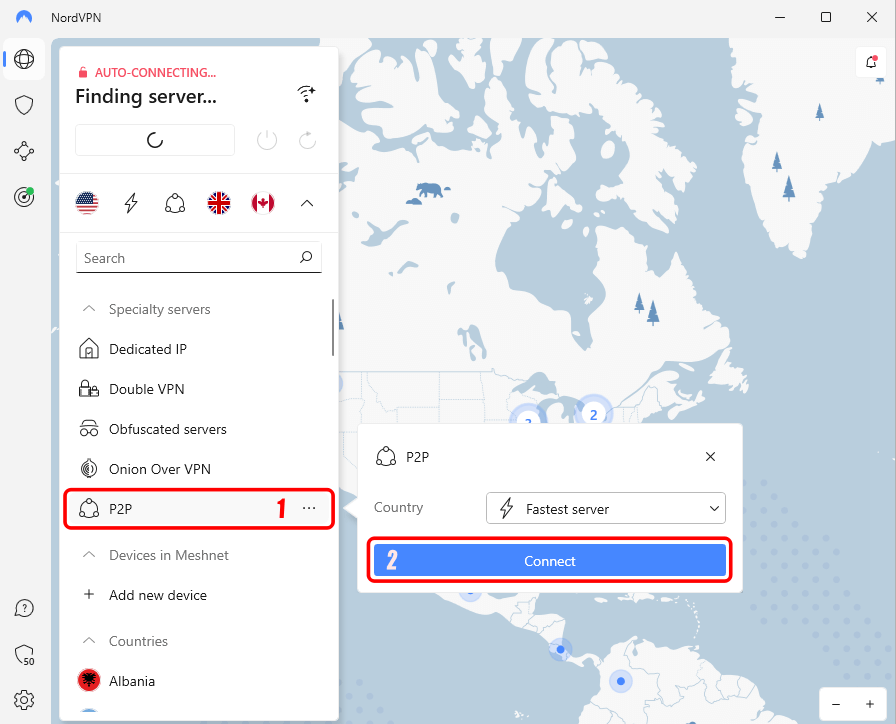
After entering the credentials and logging in, you’re greeted with NordVPN’s dashboard. Now head to the quick access menu and select “P2P,” which auto-connects you to the fastest P2P server.
You can manually connect to any desired P2P server by clicking on the three dots next to P2P to extend the menu and select a desired P2P server from the drop-down.
After selecting the desired P2P server, click on the “Connect” button to connect to the P2P server.
b. Enable the Internet Kill Switch to enhance security.
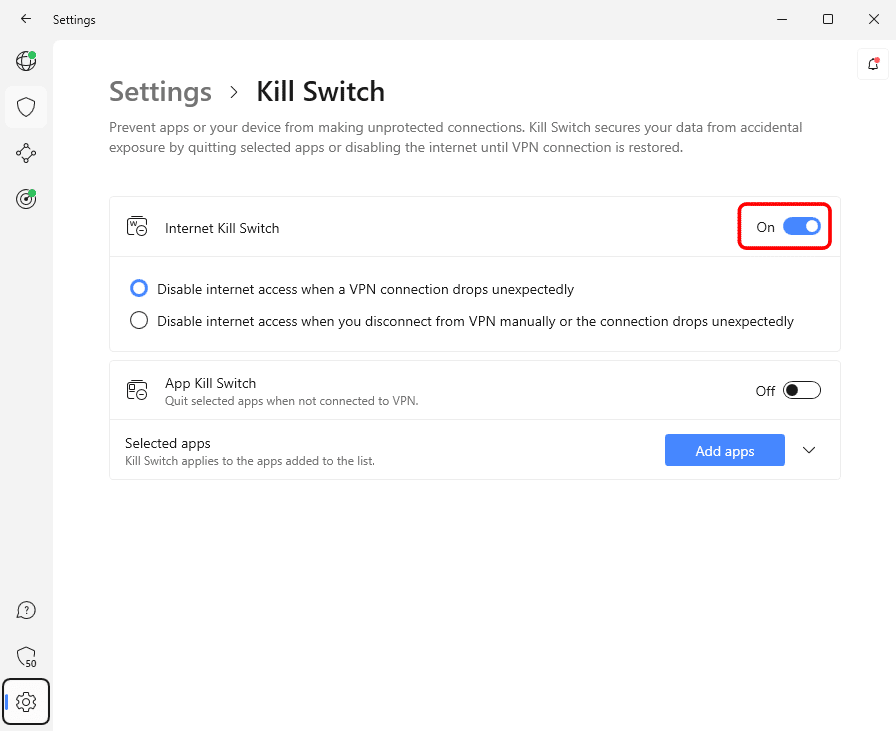
Look for the gear icon on the dashboard to open NordVPN’s settings. Now select the “Kill Switch” from the list of other options. By doing so, a new menu features all the options associated with the Kill Switch.
Now look for the toggle beside the option “Internet Kill Switch” and enable it. Upon enabling the option, the security is enhanced as NordVPN’s Kill Switch is now active.
The user can apply Kill Switch to specific apps by clicking on the Add apps button and selecting apps from the list.
These three steps can help you securely connect to the P2P servers of NordVPN. As per NordVPN, these three steps are enough for secure torrenting. If you’re unsatisfied with the level of anonymity and security offered by P2P servers, opt for the other method, which involves using a SOCKS5 proxy.
If you’re having difficulties connecting to NordVPN’s P2P servers, check out the NordVPN video for detailed information about the P2P network.
b. Using SOCKS5 proxy on qBittorrent:
In this approach, the user uses proxies along with NordVPN for torrenting on the qBittorrent. NordVPN provides the NordVPN qBittorrent-related host address and proxy details on their official website.
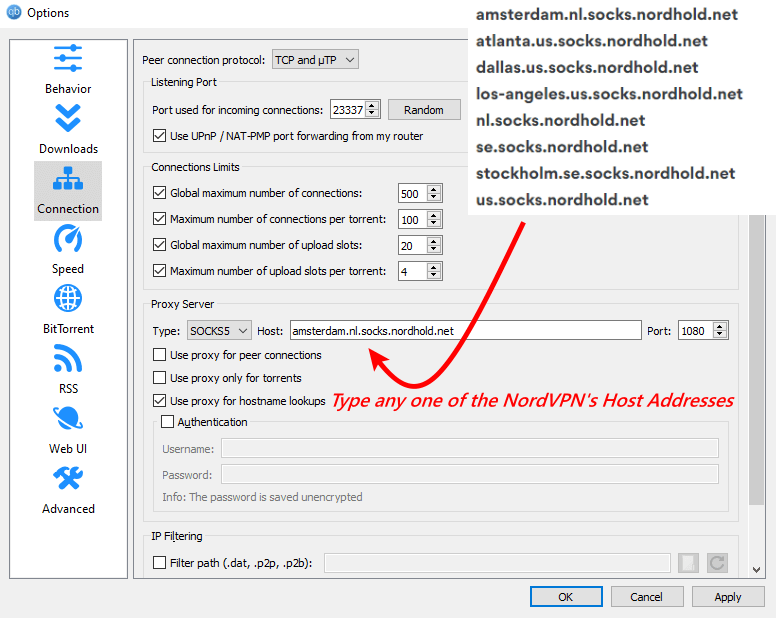
Here is the list of host addresses offered by NordVPN;
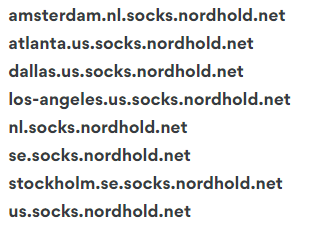
The downside of these host addresses and the proxy is slow speeds and problems maintaining a stable connection. To prevent this, you can opt for RapidSeedbox‘s high-success rate proxy, which includes a fast, stable, anonymous HTTP & SOCKS5 proxy compatible with the qBittorrent.
Here is a detailed walkthrough on how to set up NordVPN qBittorrent through SOCKS5 proxy;
b.1 Install qBittorrent and its services.
Search for qBittorrent on your web browser, visit qBittorrent’s download page, and download the setup file. Now run the setup and leave the defaults, as usual, to properly install all the qBittorrent services.
- Open the qBittorent settings – Connection Preferences.
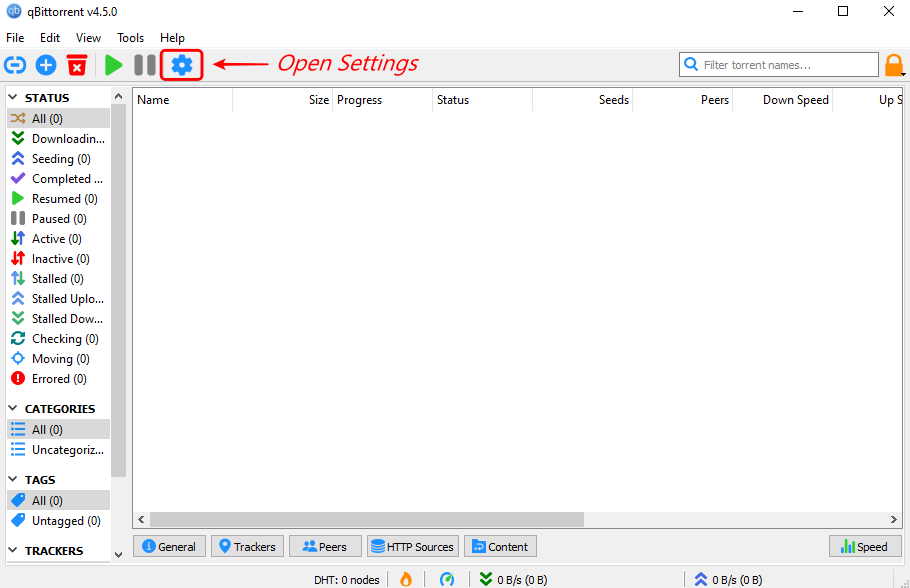
After successful installation, open the qBittorrent and look for the gear icon on the dashboard to open Settings. On opening qBittorrent settings, check for the option “Connection” to open all the settings associated with connection preferences.
b.2 Change the Proxy Server type.
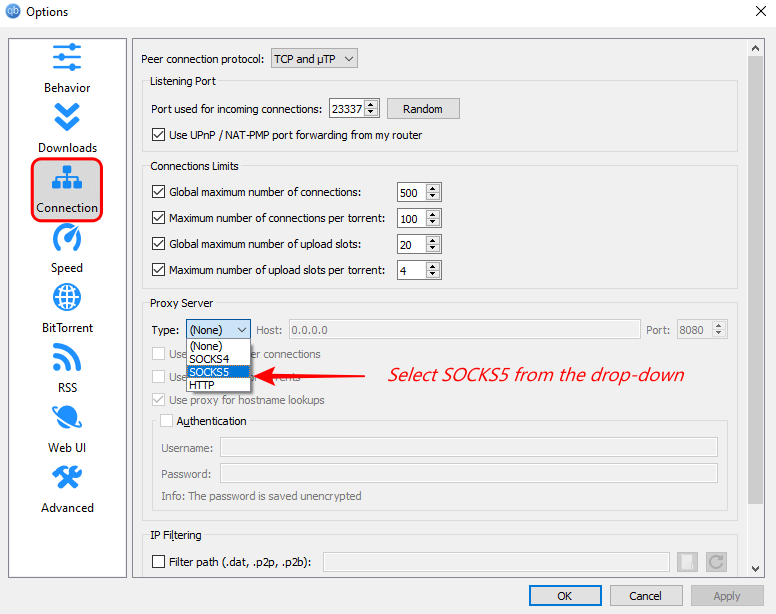
In the connection preferences, look for the “Proxy Server” section. Make changes to the proxy type by selecting “SOCKS5” from the drop-down menu.
Consider checking out: The Best qBittorrent Settings
b.3 Modify the Port number.
The port number is set to 8080 by default on the qBittorrent. Now modify the port number to 1080 (Suggested by NordVPN).
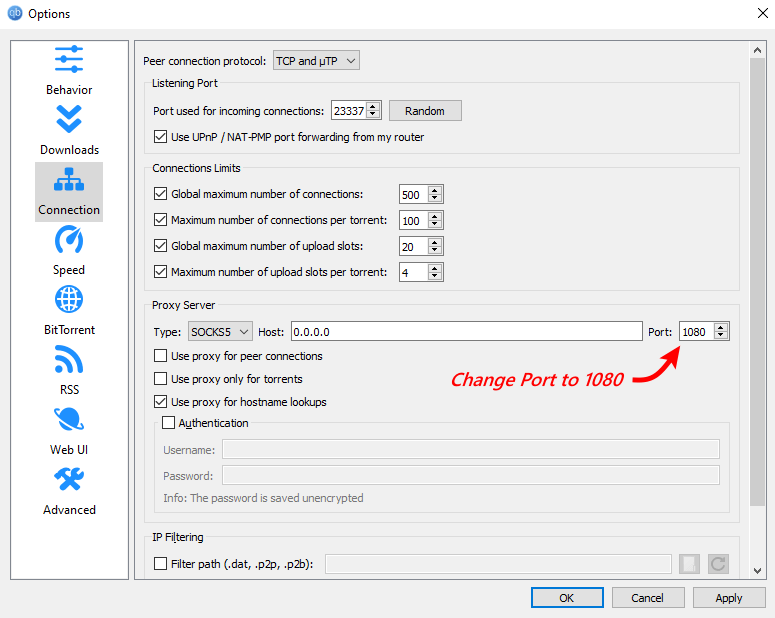
b.4 Update the Host Address.
Update the host address offered by NordVPN in the given box beside the “Host.” Usually, these host addresses are unstable and don’t provide neck-breaking speeds.
To achieve the best anonymity and download speeds with outstanding security, provide the RapidSeedbox proxy. The best part of the RapidSeedbox proxy is the affordable plans; hence, you can torrent with peace considering they are very secure and provide a stable connection.
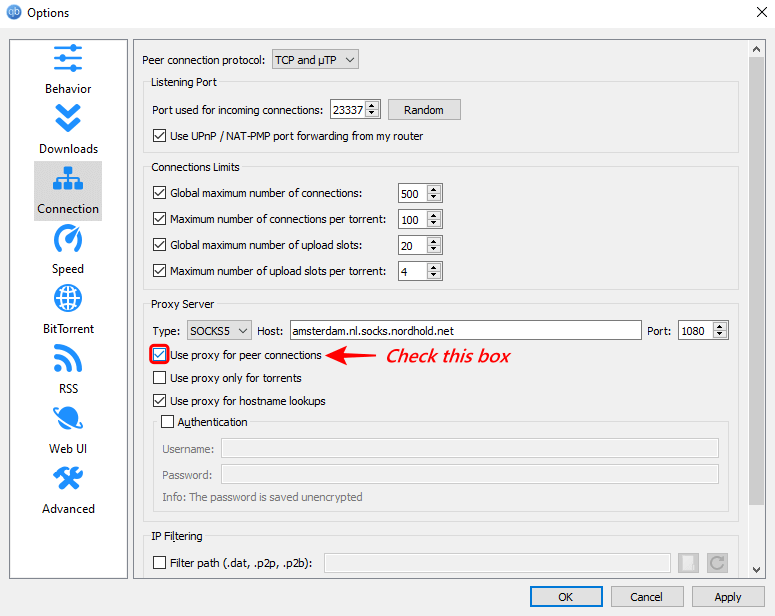
b.5 Don’t forget to tick the “Use proxy for peer connections.”
All these changes would be wasted if the option “Use proxy for peer connection” is not checked. Hence make sure to check the box before applying the changes.
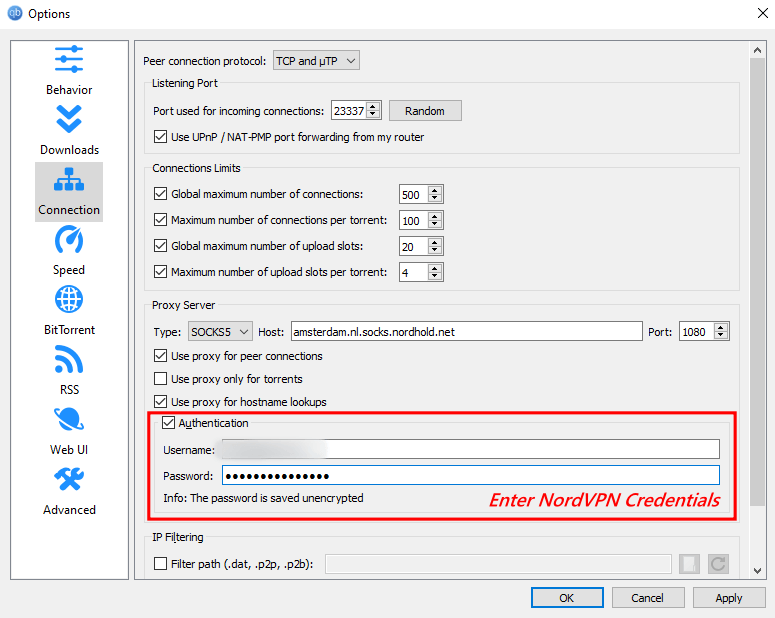
b.6 Enter the NordVPN configuration credentials.
NordVPN’s configuration credentials are different from the login credentials. Head to Nord VPN’s website by logging in to get configuration credentials access. Check for the option “Services” and then click on NordVPN.
Now you’re displayed with all your personal information, including configuration details, at the bottom of the web page. Copy these credentials and use them in the Authentication section and click on Apply followed by OK to use the SOCKS5 proxy on qBittorrent.
By following these steps, you can use the SOCKS5 proxy on qBittorrent. You can follow the first method if these advanced steps are challenging to implement.
As the approach of SOCKS5 is complicated, it is common to make some mistakes. Hence make sure to cross-check each step and make the changes carefully. If you want more information regarding SOCKS5, check out our following SOCKS5 guide.
To ensure safe torrenting, verify if the NordVPN qBittorent is well implemented and established by checking out these verification methods before downloading any torrent on the qBittorrent.
5. How to Verify if NordVPN is Connected with qBittorrent?
No test was explicitly made to check if NordVPN is appropriately connected with qBittorrent. Instead, the user can opt for a few popular verification methods to test whether the qBittorrent VPN is well established by checking and analyzing the results.
Here are the three main verification methods to check out before downloading a torrent through qBittorrent;
- DNS Leak Test
- Speed test
- Torrent Address Detection
a. DNS Leak Test:
The DNS Leak test verifies whether the DNS queries are made through the ISP or VPN servers. A leak can be identified if the user’s IP remains the same and isn’t replaced with the VPN-assigned IP.
We have connected our device to a server using NordVPN’s quick connect feature and verified if there are any DNS leaks. Here is an image of the results;
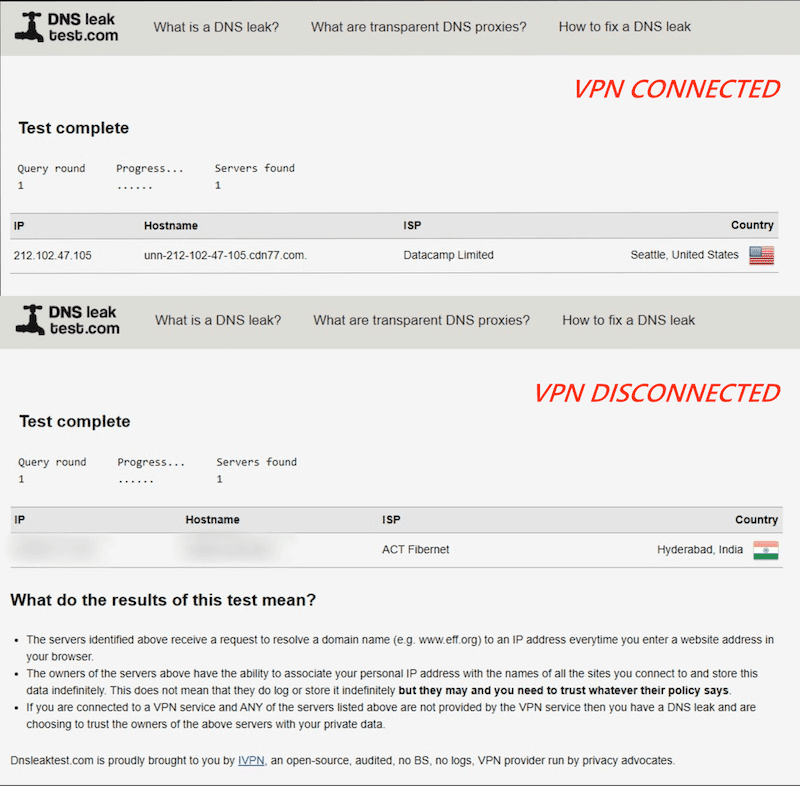
The image shows that the IP, Hostname, ISP, and Country are changed upon connecting to NordVPN. After disconnecting from the server, everything is back to default.
A DNS leak can be confirmed if the default configurations are remained the same after connecting to the VPN.
b. Speed Test:
Connecting to a VPN usually reduces the network speed, and the latency also increases. Even though there is a reduced network speed, the download speeds are breakneck while downloading a torrent.
Here are the Speed test results before and after connecting to a VPN.
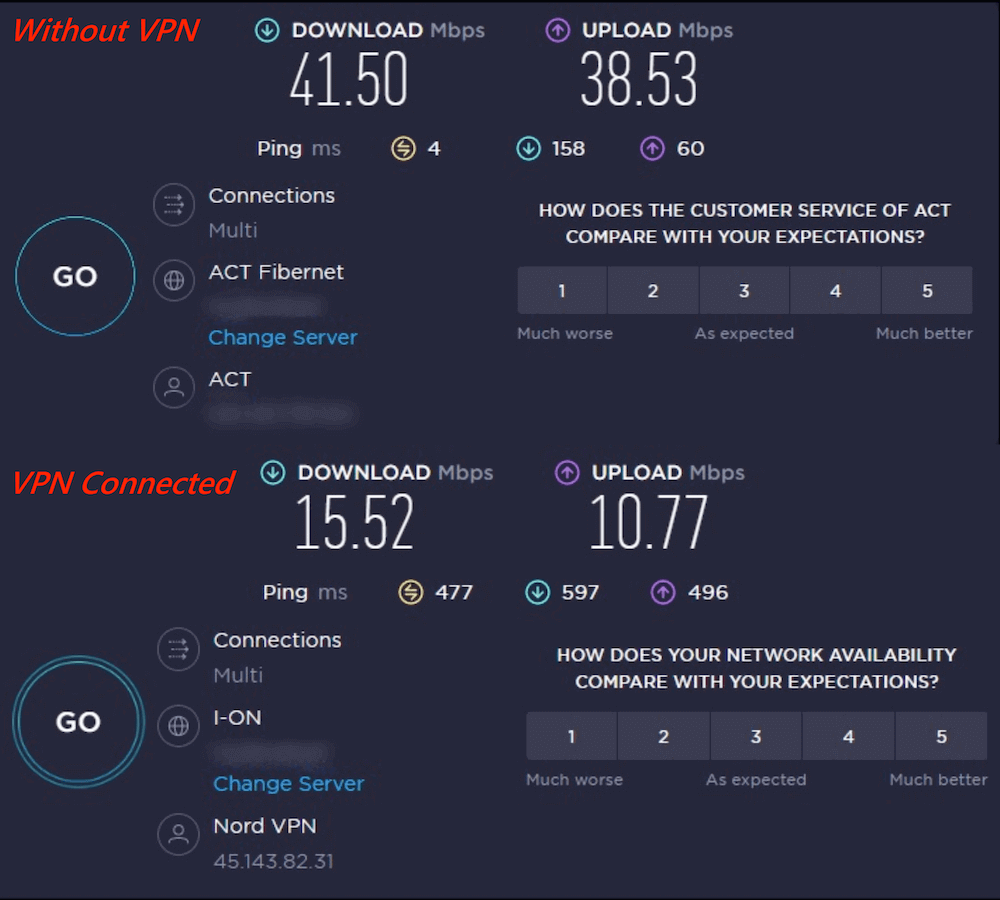
This small verification method can help the user realize if the VPN is turned on, as the speeds are always reduced when connected to a VPN server.
c. Torrent Address Detection:
This verification method must be checked before downloading a torrent after setting up qBittorrent VPN (NordVPN qBittorrent), as it prevents IP leaks. To check for IP Leaks is simple, and the user has to download a test magnet link.
The Torrent IP is generated upon downloading the test magnet link, which must be similar to the IP listed in the tracker’s tab. The VPN isn’t well established if there is any difference in IPs or if the Torrent IP and browser IP are not identical.
Here are steps on how to perform this test;
- Download the magnet link and wait for the Torrent IP to generate.
- Upon pressing the magnet link, allow access to open the qBittorrent.
- Now check for details generated by IPleak, after downloading the magnet link.
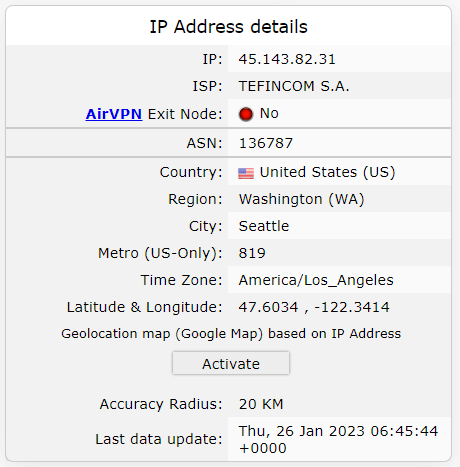
- Now verify the geographical IP address of the location through the IPlocation by comparing it with the details generated by IP Leak.
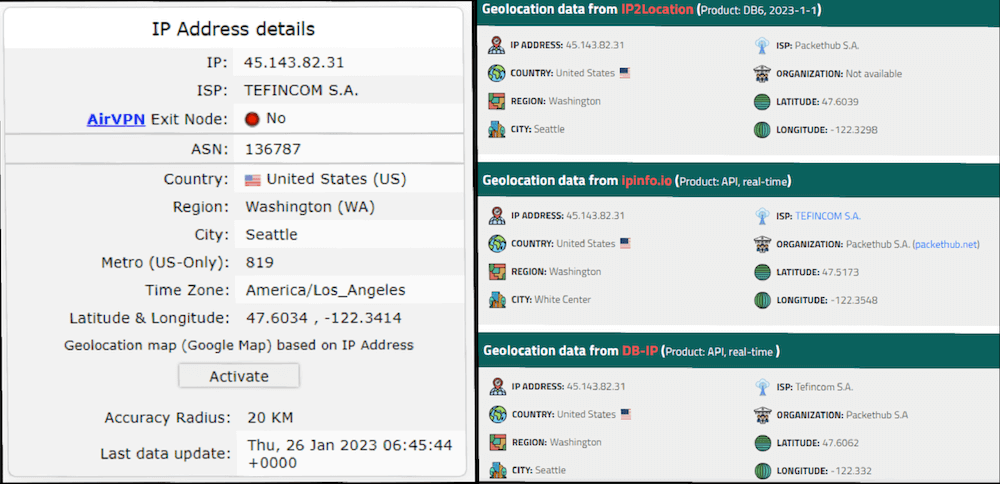
Upon comparing the results, you can see that the IP Address and the location are similar, which means that you have successfully configured NordVPN qBittorrent. If there is any dissimilarity, make sure to re-configure the qBittorrent VPN – NordVPN by following any of the above methods listed in the section on how to set up NordVPN for qBittorrent.
Using qBittorrent with NordVPN?
Enhance your torrenting setup with RapidSeedbox’s high-speed seedboxes. Enjoy faster downloads, improved security, and seamless integration, ensuring a smooth and efficient torrenting experience with qBittorrent.
6. Conclusion
Using BitTorrent protocols and its clients to upload and download torrents might be easy if done good research. Still, the user might be a victim of the dangers associated with malicious torrent links if done improperly.
Most malicious torrent links are infused with trackers and malware that are far more dangerous than the ones on the web. If the user turns victim to these dangers, there might be data loss, and all the devices linked under the same account are also affected.
Cybercriminals use the data by selling it to miners, holding sensitive information for ransom, stealing money through unauthorized transactions, etc. You can eliminate these unfortunate outcomes with the help of an excellent qBittorrent VPN.
For this purpose, we have selected NordVPN qBittorrent to download torrents by staying anonymous and secure. All features of the NordVPN function just as advertised and are efficient and effective while torrenting. The only drawback is the instability noticed while torrenting using the SOCKS5 proxy on the qBittorrent.
For enhanced anonymity, improved security, and better speeds, use RapidSeedbox proxy, which is compatible with BitTorrent clients and better than the NordVPN-suggested SOCKS5 proxy.
Great info except for the very last step (and most important). The “magnet link” is just an image. There is no magnet link posted to this article. Otherwise, nice job on the explanation!