A SOCKS5 proxy works as an intermediary between your device and the internet. It conceals your IP address and safeguards all data in transit. Operating similarly to a VPN (except for the encryption), the SOCKS5 proxy also shields your identity. Plus, when located in an offshore data center, it enables access to geo-blocked content and circumvention of censorship.
To learn more about SOCKS5 Proxy, join us in this blog post. You’ll discover the ins and outs of SOCKS5 proxies, their benefits, and disadvantages. With this information at hand, you’ll be able to make better decisions about integrating them into your daily online activities.
Without further ado, let’s dive in!

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents.
- Introduction to SOCKS5 proxy.
- Five benefits of using the SOCKS5 proxy
- Popular use cases of the SOCKS5 proxy.
- What are the differences? SOCKS5 vs VPN.
- Get started with a SOCKS5 proxy.
- SOCKS5 proxy: Frequently Asked Questions.
- Final Words and recommendations
1. Introduction to SOCKS5 proxy.
a. What is SOCKS5?
A SOCKS5 (SOCKet Secure version 5) proxy is a type of proxy server that intercepts traffic flowing between your computer and a destination (web app or site). When the SOCKS5 proxy intercepts your traffic requests, it masks your “source” IP address with its own. It then forwards this request to the right destination using its own IP. A SOCKS5 proxy server is a great alternative to a VPN, as it also protects your traffic from exposing sensitive information.
Technical fact: SOCKS is a network protocol based on the old Secure Sockets. It was designed to improve client-server applications using TCP or UDP connections. It works at the session layer (layer 5 of the OSI model), so it can handle different types of traffic requests, including HTTP, FTP, SMTP, etc., and applications like P2P/torrenting, web browsing, email, and more.
b. How does a SOCKS5 proxy works?
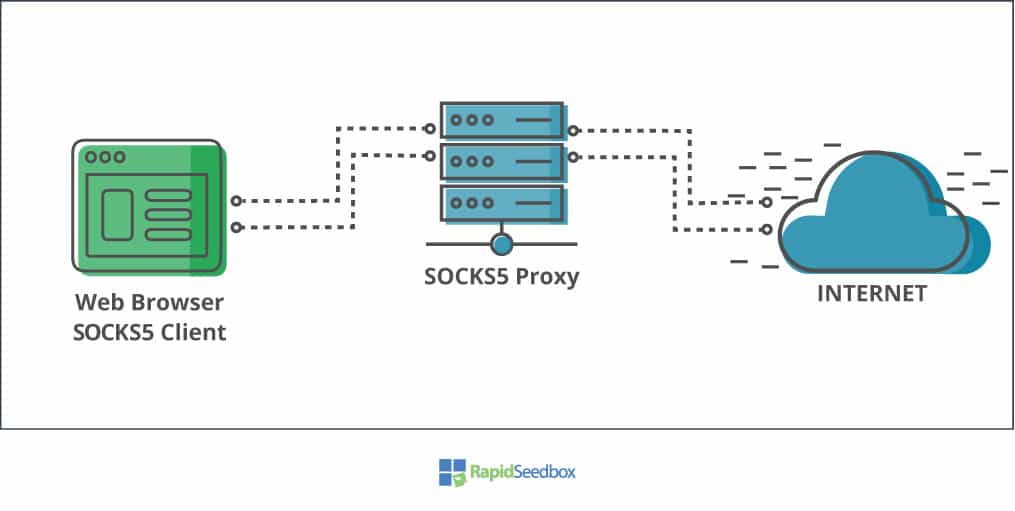
The SOCKS5 proxy server acts as the intermediary between two different networks (either private or public).
The common scenario for a SOCK5 proxy (private > public) is as follows (Refer to the picture below):
- Your SOCKS5 client (such as a web browser, gaming platform, or torrent platform) opens a TCP (or UDP) connection to the SOCKS5 proxy server.
- The SOCKS5 proxy receives the traffic from your SOCKS5 client, performs some action (changing packet headers, hiding IP, etc), and forwards it to the destination, normally on the Internet. The SOCKS proxy server establishes a new (TCP or UDP) connection with a new IP address to the website or app’s server.
- The website or app located on the internet, replies to the SOCKS5 proxy, without knowing the real source of traffic was your SOCKS5 proxy. The SOCKS5 proxy performs its magic, by mapping the incoming responses from the internet and forwarding all to the source, your computer.
c. What can you use a SOCKS5 proxy for?
SOCKS5 proxy servers can be used by anyone from individuals to Small-to-Medium Businesses, to enterprises. It all depends on the application.
- If you are an individual looking for the right trade-off between online anonymity and speed use a SOCKS5 proxy. If you use applications that depend on speed such as P2P/torrenting, streaming, gaming, etc, and do not contain sensitive data, a SOCKS5 proxy is for you. SOCKS5 proxies are also useful if you are looking to bypass geo-restricted content or enforced censorship.
- SOCKS5 proxies are also potential security solutions for companies or large businesses. It can be useful for letting remote users connect to internal networks. With a SOCKS5 proxy in place, network admins, won’t have to modify firewall rules in order to let those remote users in, they would only enforce authentication via the SOCKS5 proxy. Additionally, a SOCKS5 proxy can also be used for data scraping, SEO campaigns, social media marketing, test websites and ads, threat hunting, and more.
2. Five benefits of using a SOCKS5 proxy.
SOCKS5 proxies have more flexibility and security than any other type of proxy. Generally, you could use a SOCKS5 proxy server when you need to achieve the right balance between two desirable (but often incompatible features): anonymity and speed.
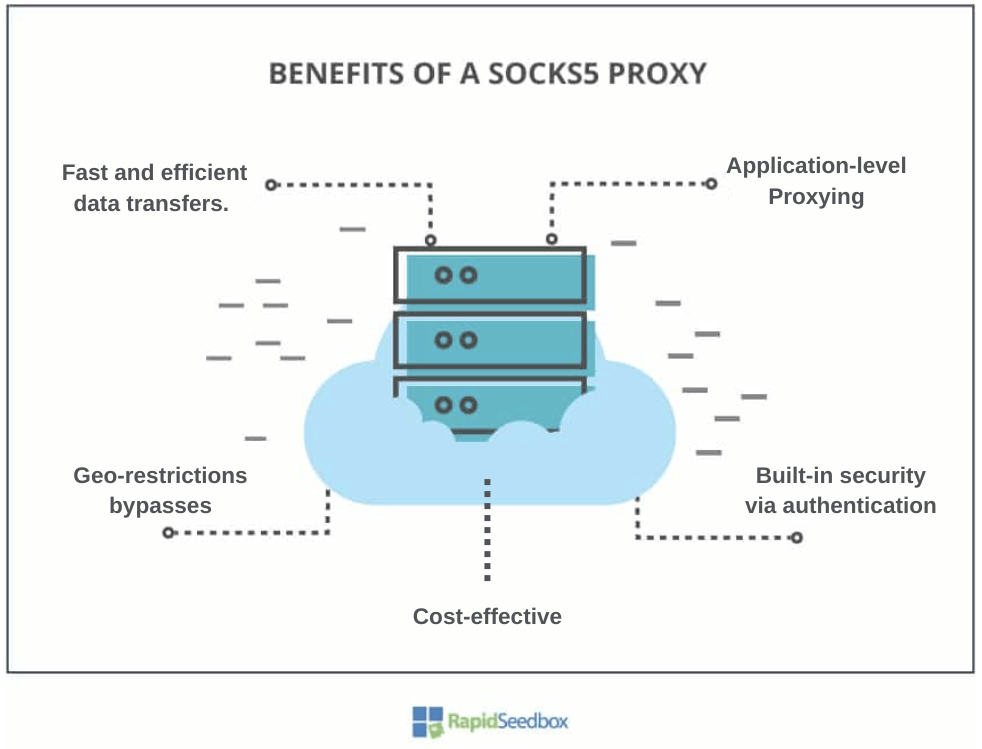
Below are five common benefits of using a SOCKS5 Proxy.
- Fast and efficient data transfers.
- Cost-effective (Generally cheaper than VPNs.)
- Application-level proxying.
- Geo-restrictions bypasses.
- Built-in security via authentication.
a. Fast and efficient data transfers.
SOCKS5 proxies don’t perform heavy encryption like VPNs. So, without all this additional encryption overhead, the SOCKS5 proxy’s packets are relatively smaller and easier to process. This “lower overhead” ultimately leads to better performance and speed. SOCKS5 proxies are great for applications that require high bandwidth, like P2P/torrenting, online video games, streaming, VoIP, etc.
b. Cost-effective (generally cheaper than VPNs)
SOCKS5 proxies are generally considered to be cost-effective privacy and security solutions. This cost-effectiveness arises from several factors. For example, SOCKS5 proxies have no encryption overhead— their primary focus is on routing traffic through the proxy server. In addition, since SOCKS5 proxies offer fewer features than technologies like VPNs, they require less server infrastructure.
c. Application-level proxying.
An advantage of SOCKS5 proxies is that you can selectively use them for any traffic (TCP or UDP). Basically, you can configure proxy settings on a per-application basis (i.e. web browsers, torrent clients, game consoles, etc). Instead of having your entire traffic go through the proxy, you can instead choose which applications or services should route their traffic through the proxy.
d. Geo-restrictions bypass.
SOCKS5 proxies can help you access content that is restricted based on your geographical location. When you use a SOCKS5 proxy that is located in another country you’ll be able to either bypass your local geo-restrictions or access content built specifically for that country. Connecting to SOCKS5 proxies on another country, you can make it appear as though your traffic originates from that location. This is an effective way to bypass geo-blocks and access region-specific content.
e. Built-in security via authentication.
SOCKS5 proxies provide authentication. Users connecting to a SOCKS5 proxy server can be authenticated to prevent unauthorized access. Authentication is quite useful when you are accessing a shared proxy server, so you know that other users on the server are trusted. Although the default mode is to not enforce authentication when a client connects to the server, admins can configure authentication. The proxy server can require a username and password to connect clients.
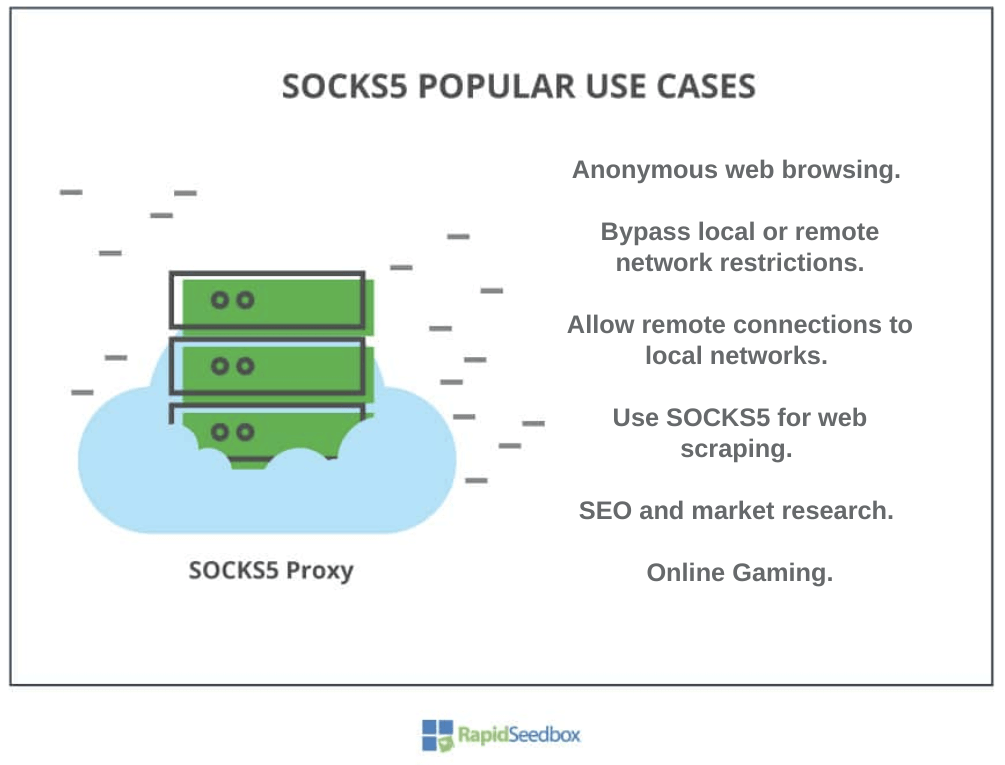
3. Popular use cases of the SOCKS5 proxy.
We briefly defined the applications of a SOCKS5 proxy in the first section, but now let’s define with more clarity, what are some of the most popular use cases of SOCKS5 proxies.
- Anonymous web browsing.
- Bypass local or remote network restrictions.
- Allow remote connections to local networks.
- Use SOCKS5 for web scraping.
- SEO and market research.
- Online Gaming.
a. Anonymous and private web browsing
For individuals that prefer a certain degree of anonymity (not encryption) while web browsing SOCKS5 proxies, provide a fantastic solution. SOCKS5 proxies route the user’s traffic through the server masking their true IP address. This makes it more difficult for websites to track a user’s online activities. Just keep in mind, that SOCKS5 proxies do not encrypt traffic.
b. Bypass local or remote network restrictions.
A SOCKS5 proxy can be used to circumvent local Internet restrictions or censorships created by governments, schools, or workplaces. Any firewall filtering traffic will most likely have no idea of the SOCKS proxy, so it will allow traffic to flow to the proxy. A SOCKS5 proxy can also help you circumvent remote restrictions from applications and websites defined by geo-restrictions, IP bans, rate limits, or blacklists. The proxy server (in another country) serves as an intermediary between your device and a destination, circumventing remote service restrictions. Before bypassing restrictions, always read and respect the Terms of Service of a site or network.
c. Allow remote connections to local networks.
A SOCKS5 proxy can be used for remote users wanting to securely access an internal network. Setting a local SOCKS5 proxy with authentication will help establish secure inbound connections from the Internet to the internal network. As mentioned in the first section of this guide, SOCKS5 proxies help network admins reduce firewall management, so they don’t have to change rules in order to grant users access to networks.
Note: a SOCKS5 proxy is not a replacement for a firewall. Firewalls are still needed to protect your network and infrastructure.
d. Use SOCKS5 for web scraping.
SOCKS5 proxies are ideal for tasks like web scraping. Online web scraping uses software to automatically scrape data from sites, extract unstructured data, and provide structured results. Using proxies to scrape web data is the best way to automate efforts. For example, a rotating IPv6 proxy will help you bypass detection from anti-data-scraping technology and still respect the site’s ToS. Proxies will produce efficient, errorless, and fast results.
e. SEO and marketing research.
Marketers and SEO professionals can find lots of benefits from using SOCKS5 proxies. For example, they can view search engine results from different locations. This helps them tailor marketing strategies based on regional preferences and trends. In addition, with the help of a web scraper, marketers can also research audiences from Facebook and Twitter scraping. Plus when it comes to SEO, marketers can improve their site’s standing on search engines by using an SEO proxy, so they can study competition, scrape data, etc.
f. Online gaming.
Another popular common use case of SOCKS5 proxy servers is online gaming. You might want to use a SOCKS5 proxy if you are a gamer and want to reduce lag and improve online gaming performance. Connecting to a proxy server that is close to the game server’s location can help gamers reduce latency and improve their gaming experience. SOCKS5 proxies may also help workaround the IP bans unfairly imposed on gamers, access geo-restricted game servers, bypass local network limitations, and more. Learn more about this on “what is a proxy on PS4?“
5. What are the differences? SOCKS5 vs. VPN.
A SOCKS5 proxy is one of the best alternatives to a VPN. Still, VPNs and proxies are completely different technologies— designed for different purposes. The clearest distinction between SOCKS5 and VPNs is that VPNs send traffic through an encrypted tunnel, while SOCKS5 proxies don’t.
What is better, a VPN or a SOCKS5 proxy?
Again, both technologies were created for different purposes, so which one is better? would depends on your requirements and resources. Each piece of technology can be better for different circumstances. For more on this, check out our comprehensive comparison between VPNs vs Proxy.
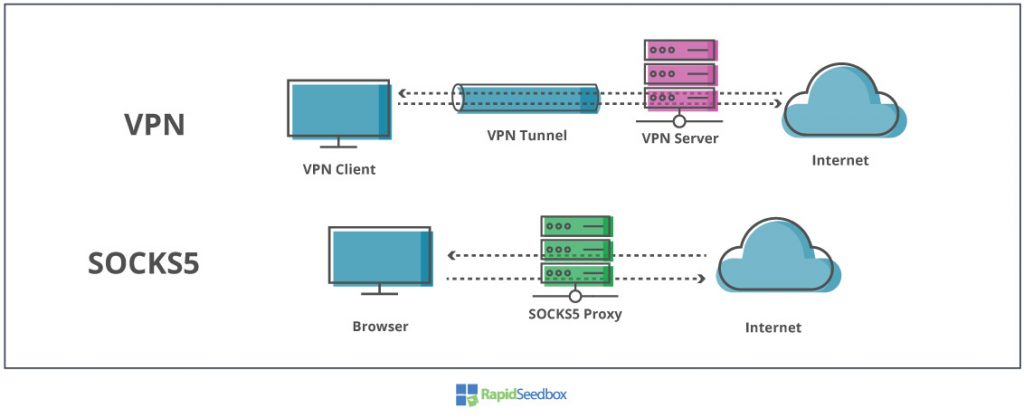
VPN vs SOCKS5 Comparison Table:
| Technology. | OSI Layer. | Encryption | Security | Type of traffic | Speed | Security. | Price |
| SOCKS5 | Layer 5 | Only with SSH, HTTPS, etc | Only authenticates. | App-level | Faster than VPN | Changes IP | Cheaper than VPN |
| VPN | Layer 3 | Built-in | Encrypts data. | Entire Internet connection | Slower than a proxy. | Changes IP | More costly than a proxy. |
When to use a SOCKS5 proxy or VPN.
- A VPN encrypts your entire Internet connection, making them more secure than proxies. VPNs are suitable for handling more sensitive data (banking, trading, HR, etc) when you connect to public networks.
- SOCKS5 proxies, on the other hand, are suitable for Internet-based applications that need speed, like games, P2P/torrenting, VOIP, streaming, etc, but that don’t handle sensitive information.
Both technologies are good for bypassing geo-restrictions or local-imposed network limitations. Also, both VPNs and SOCKS5 are good “remote access solutions” to let remote users connect to local networks.
SOCKS5 proxy vs VPN: P2P/Torrenting
Both VPNs and SOCKS5 proxies are great privacy tools that can be used for P2P or torrenting. Both will hide your P2P activity in some way or the other.
- Hiding torrent data (protocols and ports) from local ISP. A VPN will encrypt data (at layer 3), so your ISP will not be capable of identifying P2P traffic. If you are using a SOCKS5 proxy, your ISP could identify your P2P traffic (unencrypted traffic).
- Hiding IP from the torrent swarm. Both the VPN and the SOCKS5 proxy server’s IP will be shown in the torrent swarm. So even though you are downloading legit content, roaming copyright trolls spying torrent swarms will be able to get your real IP address. A solution to this is to avoid public torrent trackers and use only private trackers.
- Speed. When it comes to speed, SOCKS5 does encrypt data, so it can be much faster than VPN for P2P.
What is cheaper, VPN or SOCKS5 proxy?
SOCKS5 proxies require less infrastructure (no encryption overhead) to work than VPN technology— therefore SOCKS5 tend to be cheaper. In addition, there is no need to have SOCKS5 client software (as you would in VPNs)— all you need to do is configure the application with proxy information, like IP address, protocol, and port. Additionally, proxies work fine with IPv6 addressing (which are cheaper than IPv4s), VPNs on the other hand have potential data leaks if used with IPv6 (or dual-stack).
Looking to optimize your online privacy with a SOCKS5 proxy?
Beef up your security and performance with RapidSeedbox’s premium SOCKS5 proxy services. Enjoy fast, anonymous browsing and seamless data transfers, backed by our expert support.
6. Get started with a SOCKS5 proxy.
To use a SOCKS5 proxy on your computer, all you need to do is find a reliable SOCKS proxy provider and get the proxy’s information, such as IP address (or hostname), protocol (SOCKS5), port number, and authentication credentials (if necessary).
a. The best reliable SOCKS5 server providers.
- Rapidseedbox: A provider that stands out as a versatile and customer-centric leader of SOCKS5 proxies. Rapidseedbox offers both IPv4 and IPv6 proxies. Their proxies features range from dedicated IPv4 options to unlimited bandwidth, and IP rotation. RapidSeedbox attends to diverse needs, from SEO optimization to data scraping and market research. Their 24/7 customer-driven support and a 14-day money-back guarantee underline their commitment to user satisfaction.
- Free-proxy or Free Proxy List. If you are looking for free SOCKS5 proxies, you can find available lists online that provide you with a selection of free proxies. While these lists offer free access proxy services, it’s important to know about their potential security risks and unreliable connections. You should be aware when free proxy lists. SOCKS5 proxies are generally shared and might lack the performance, privacy, and support features offered by dedicated SOCKS5 proxy providers.
- Bright Data: A popular provider with an extensive proxy pool of over 72 million real residential IPs (proxies), 1.6 million data center IPs, and 7 million+ 3G/4G mobile IPs. Bright Data offers global coverage across 195 countries.
- Oxylabs: A leader in residential IP addresses. Oxylabs offers more than 2 million dedicated datacenter IPs and 100 million residential IPs (TCP-only). Additionally, it has extended coverage of about 188 countries. Key features include a usage stats dashboard, dedicated Account Managers, and session control.
- Smartproxy: Specializing in dedicated datacenter proxies, Smartproxy offers 400,000 US IPs and features sequential and non-sequential IP options.
b. Configuring the SOCKS5 proxy on your device.
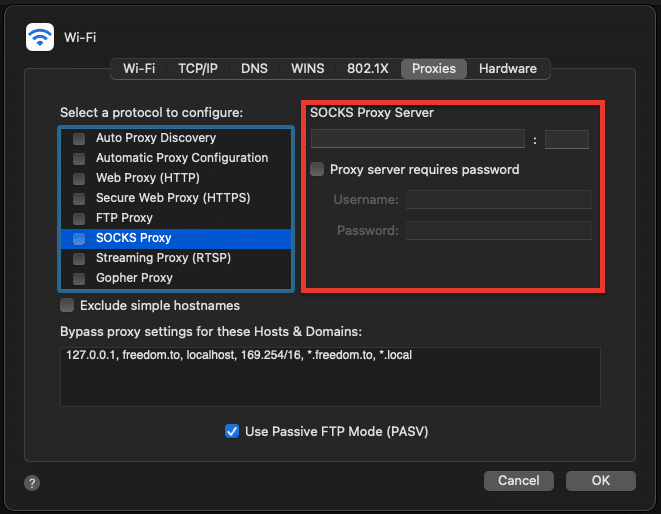
i. Configure SOCKS5 on a macOS.
To configure SOCKS5 Proxy Server in a macOS for your default browser, you need to go to System Preferences > Network > (choose your interface) > Advanced > Proxies.
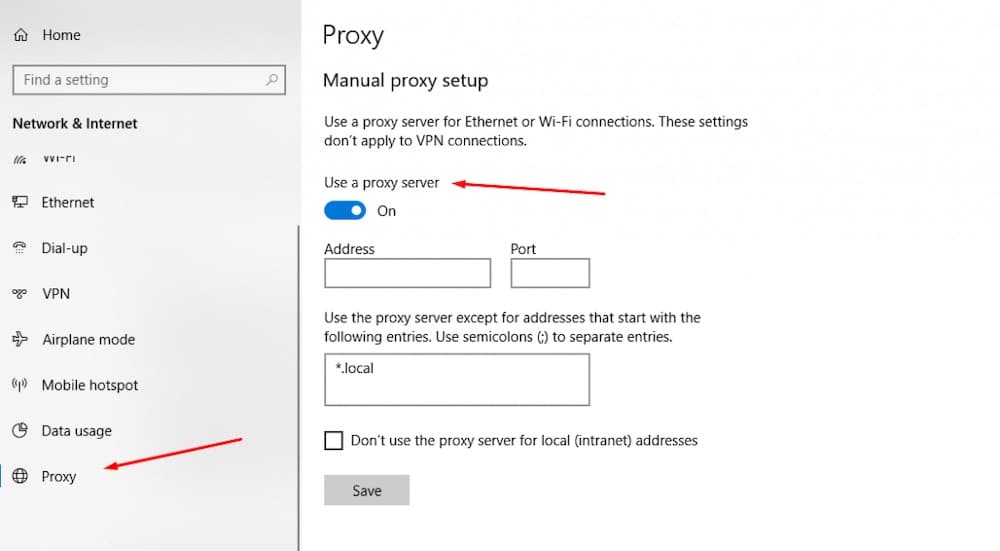
ii. Configuring SOCKS5 on a Windows.
To configure a SOCKS Proxy Server on Windows 10, go to: Settings > Network & Internet > Proxy.
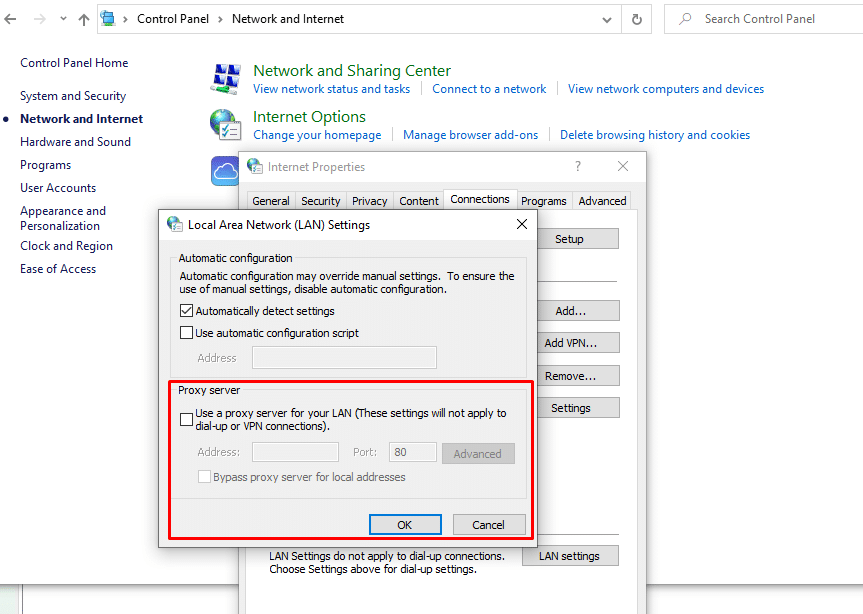
Or you can also go through:
- Control Panel > Network and Internet > Internet Options > Connections “tab” > LAN Settings > Proxy server.
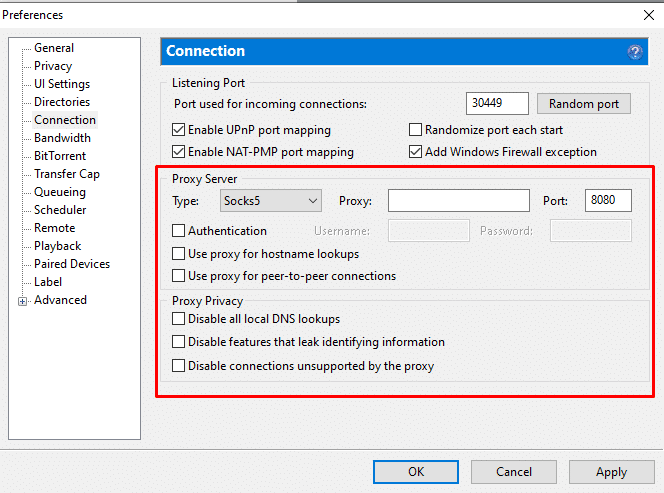
iii. Configure SOCKS5 on uTorrent.
Of course, you can also configure torrent platforms like uTorrent, qBittorrent, or BitTorrent, to use a SOCKS5 proxy server to route its traffic.
To configure a SOCKS5 proxy for Torrenting in uTorrent, go to Preferences > Connection > Proxy Server.
For more information on setting up a proxy for your torrents, check the comprehensive guide to Torrent proxy.
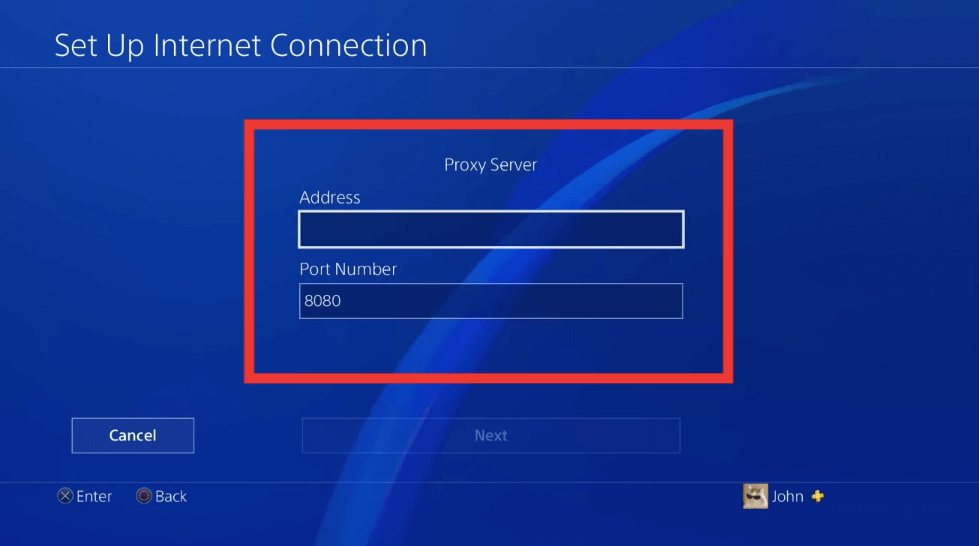
iv. Configure SOCKS5 proxy on PlayStation 4 (PS4)
PS4 allows you to configure a SOCKS5 proxy server for your internet connection. To set up a proxy manually on your PS4, follow these instructions:
- Go to the PS4 home screen.
- Navigate to “Settings” then select “Network”
- Under the “Network” menu, follow the instruction until you see the proxy server configuration. Enter the proxy server’s IP address and port number.
- If the proxy server requires authentication (such as in the case of SOCKS5 proxies), enter the username and password given by your proxy provider.
7. SOCKS5 proxy: Frequently Asked Questions.
a. If there is SOCKS5, whatever happend to SOCKS4?
SOCKS4, the older version of SOCKS5 does not support authentication or UDP connections. SOCKS5 is an optimized version of SOCKS4. The SOCKS5 protocol, approved by the IETF (RFC 1928), supports a variety of authentication methods and provides means to forward UDP packets. SOCKS5 can establish a TCP connection with authentication, so only authorized users can access the proxy server. Additionally, it can use Secure Shell (SSH) encrypted tunneling to enhance security.
b. SOCKS5 vs HTTP proxy?
Although both types of proxies are intermediaries of traffic, they perform differently. HTTP proxies are considered high-level (OSI layer 7) because they only work with HTTP or HTTPS protocols (ports 80 and 443) so they can only be used through your web browser. HTTP proxies can only forward HTTP requests and in some cases modify certain headers. SOCKS5 proxies, on the other hand, are considered lower-level, as they can take almost any type of traffic or protocol. These types of proxies are suitable for a wide number of applications. Additionally, the fact that SOCKS5 can forward TCP and UDP traffic, and can be used with authentication, makes them completely different from HTTP proxies.
c. Can a SOCKS5 proxy’s security be strengthened?
Dedicated (non-shared) SOCKS5 proxies can be configured to be as secure as a VPN Server. For example, by implementing a private SOCKS5 with an SSH-encrypted tunnel, you can drastically improve the security of a SOCKS5 proxy. Still, keep in mind that the SOCKS5 is just a transport protocol, and by itself does not provide encryption. Still, encryption could be possible with SOCKS5, but it needs to be handled by the application itself, such as a browser (SSL/TLS) or OpenSSH (SSH).
d. Should I use a SOCKS5 proxy with a VPN?
Although you could route your local “SOCKS5-proxied traffic” through a VPN tunnel, or use the VPN server as an Internet exit node to connect to the remote proxy, the only benefit you would get is a more obscured identity. For example, if your VPN connection shuts off, the IP revealed in the destination will be the proxy’s (and not yours)— this is somehow similar to the “Kill Switch” functionality found on modern VPNs. The drawback of this “SOCKS5 via VPN” configuration is the substantial decrease in network speed.
e. What are the downsides of using a SOCKS5 proxy?
There are various downsides to using SOCKS5 proxies, but generally, these are all related to the lack of built-in encryption. With a SOCKS5 proxy, your traffic packets traveling back and forth are more exposed to data breaches and traffic inspection. In addition, when you selectively proxy application traffic, you also need to be aware that the other online activities (i.e. new applications) will be unprotected.
Looking to optimize your online privacy with a SOCKS5 proxy?
Beef up your security and performance with RapidSeedbox’s premium SOCKS5 proxy services. Enjoy fast, anonymous browsing and seamless data transfers, backed by our expert support.
8. Final Words and recommendations.
SOCKS5 proxies protect your online anonymity without compromising speed. These types of proxies are also often used to bypass network restrictions, geo-blocks, or censorships. They can also provide a good degree of security if used with authentication and can even go beyond when paired with additional encryption like SSH or SSL.
Before you go… remember!
- A SOCKS5 proxy is not a VPN. If you are dealing with highly sensitive data, such as banking, trading, etc, bear in mind that SOCKS5 proxies do not encrypt data as VPNs do So, if you are using a shared SOCKS5 proxy server never send sensitive data.
- SOCKS5 proxies are fast. As stated above, SOCKS5 proxies do not encrypt. This makes SOCKS5 proxied traffic flow with less overhead, making their data transfers faster, and less prone to errors than normal VPNs.
- Use SOCKS5 for apps that require speed and reliability. It is recommended to use a SOCKS5 proxy for things that require faster connections but could go on with a few errors (UDP), such as streaming media, torrenting/P2P, or even online gaming.
- Stay away from free SOCKS5 proxies. Free proxy servers are always shared. So they are constantly crowded with all types of users, from good to noisy neighbors. Additionally, free proxies are generally supported either by showing you tons of ads, collecting and selling your data, selling your bandwidth, or even infecting you with Malware.
A private SOCKS5 proxy, on the other hand, gives you more stability, speed, and fresh IPs that have never been banned or used before.
To test the waters with a SOCKS5 proxy start with a provider that offers a 14-day money-back guarantee.
Thank you for another great article. Where else could anybody get that kind of info in such a perfect way of writing? I have a presentation next week, and I am on the look for such information.
Thanks for the article, can you make it so I get an email whenever you publish a fresh post?
Hi there… yes, for that you would need to subscribe to our newsletter.