Today, online fraudsters use new and innovative methods to get away with illegal web scraping, ad fraud, and form jacking, making it essential for companies to use innovative solutions that can secure their digital assets.
That’s why companies are slowly switching their gears and using mobile proxies to safeguard online privacy.
But, first thing first, what are mobile proxies?
Consider these mobile proxies as your cape of invisibility! But why?
Read on to explore what mobile proxies are, how they are helping in safeguarding online privacy, and how they work, and review some tips for using these proxies.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents.
- What are Mobile Proxies?
- How Mobile Proxies can Safeguard your Online Privacy?
- How do Mobile Proxies Work?
- Tips for Using Mobile Proxies.
- Final Words.
1. What are Mobile Proxies?
Like a normal proxy, a mobile proxy is an intermediary server that allocates different mobile IP addresses to a visitor while hiding or masking their real IP address. Interestingly, these proxies make it look like the visitor is connected to a mobile network using a 3G or 4G connection.
But how does it ensure your company’s online privacy?
When you use a mobile proxy, dynamic IP addresses pass through the 3G or 4G-connected devices. This ensures all your browsing requests pass only through the second “mobile” IP address instead of your real one, keeping your real identity anonymous.
Dynamic IP addresses make your mobile proxies effective and provide more security to your company’s online privacy and data.
For more information on other proxies, check our comprehensive guide to types of proxies.
2. How can Mobile Proxies Safeguard your Online Privacy?
In the world of online privacy and connectivity, more and more companies are switching toward mobile proxies. These proxies are a game-changer as they harness the power of IPs from different mobile carriers.
While the benefits of mobile proxies go far beyond online privacy and security, here’s why businesses in every field are turning their eyes toward these types of proxies:
a. Ensures data rights management
If your company handles a huge amount of data, such proxies are a blessing in disguise for your company. Why?
These proxies ensure adequate data rights management, protect your customer information, and ensure compliance with various privacy regulations.
As these mobile proxies route your internet traffic through mobile networks, you have full control of your data flow in your company.
This level of control ensures your sensitive information remains within your authorized channels. This reduces the risk of unauthorized access or data breaches.
In short, implementing such proxies provides an additional layer of protection against potential attacks and notorious cybercriminals.
b. Protects from and performs effective web scraping
Web scraping refers to extracting large amounts of data from websites. While web scraping is not inherently malicious to your online privacy (and can be used for efficient data gathering), it can be detrimental when used for unauthorized purposes or competitive intelligence gathering.
As these proxies can identify scraping bots, they deny them access to your website, reducing web scraping practices. What’s more interesting is that these proxies make it more challenging for scraping bots to identify and extract data from your website due to the constantly changing IP addresses associated with mobile connections.
On the other hand, mobile proxies can also be used for effective and regulated web scraping. A target website looks at mobile-generated traffic, as what it is, mobile traffic, so it generally it would treat the traffic as ordinary (non-bot-generated).
c. Offers superior online security
Often, your employees may come across websites with malicious or phishing links. When your employees unknowingly click on these links, your company’s system and network become susceptible to malware.
This can soon become a nightmare, primarily if your company handles customers’ or employees’ sensitive information. That’s where mobile proxies come into the picture.
When employees unknowingly click on phishing links, your computer system or tablet remains unaffected. Instead, it’s the proxy server that comes under the attack.
Mobile proxies mitigate this risk by blocking access to these websites. Also, as these proxies conceal your real IP address, they shield you from cyber threats.
These proxies serve as your helping hand as they provide 360-degree protection to your company’s online security.
d. Provides online freedom
So, you plan to expand your business and take it to another country. But you can’t access a competitor’s website in that region. What can be more frustrating and overwhelming than this situation?
That’s where mobile proxies come to your rescue.
As these proxies have no geographical limit, they easily bypass these restrictions, giving you access to the much-need competitor’s website.
This is helpful for companies who want to understand how their content or marketing activities perform in different geographical locations. Whether it’s accessing market research data, competitor analysis tools, social media scraping, or localized websites, these proxies enable seamless connectivity regardless of geographical restrictions.
Also, for companies working in countries with strict online censorship laws, these mobile proxies bypass restrictions and provide access to banned online content.
e. Reduces instances of DDoS attacks
With random Distributed Denial of Service or DDoS attacks witnessing an increase of 67% in 2022, it’s the high-time companies that use an innovative tool to prevent and absorb DDoS attempts. Unfortunately, apart from disrupting online services, DDoS attacks have a multifold financial impact.
Mobile proxies reduce the instances of DDoS attacks by masking the actual IP addresses of your business server.
When a cybercriminal launches a DDoS attack, it targets the IP address assigned by the mobile proxy, safeguarding your actual server from the attack.
This ensures your company’s operations remain uninterrupted, ensuring your customers can access valuable information.
f. Increases network security
Apart from helping companies perform safer financial transactions, using mobile proxies can drastically increase your company’s network security and contribute to creating a vulnerability program [Learn how to build a successful vulnerability program].
By masking or shielding your company’s IP address, these proxies restrict access to information related to potential network vulnerabilities. This proactive measure not only safeguards your network from potential threats but also establishes a robust foundation for a successful vulnerability program.
When cybercriminals are unaware of how to penetrate your network settings, they may turn to another company whose network vulnerabilities they can easily exploit. This ensures the security of your company’s entire network infrastructure while actively contributing to the development of a successful vulnerability program.
3. How do Mobile Proxies Work?
After decoding how mobile proxies can safeguard your online privacy, let’s explore how these proxies work to ensure your online privacy:
- To access the internet, a mobile device first connects to a 3G/4G network tower, where the device receives an IP address. Several “other ” mobile IPs belonging to the same network will connect to the same network tower.
- Mobile proxies differ because you can use the “mobile connection” on devices other than a tablet or phone. If a device uses mobile hardware and can read a SIM card, it’s good to proceed with. For instance, many companies use mobile dongles for mobile proxies.
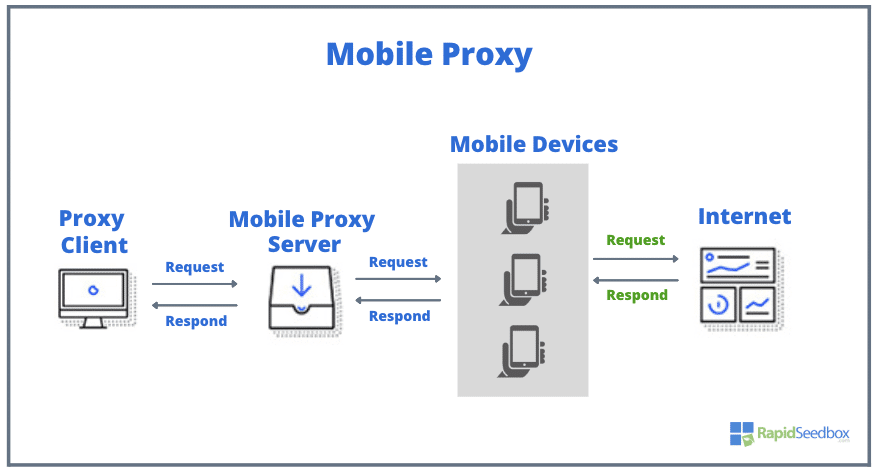
- When proxy clients (visitors) surf the internet, their request passes through the mobile proxy infrastructure. The visitor’s request then gets directed to the IP address of an actual mobile or tablet.
- This makes your request come from an actual mobile device, thereby adding an additional layer of security.
- The entire process of routing your request (or your visitor) through an actual mobile’s IP address brings in a touch of anonymity, making it difficult for target websites and services to track the actual request source.
a. What Makes Mobile Proxies Different?
The icing on the cake is that these mobile proxies use rotating IP addresses. As visitors browse information, their requests get recycled through different IP addresses connected to different mobile devices.
As the IPs are dynamic and not static, websites cannot block your IP address from accessing the desired information. They also don’t raise questions like the use of static IP addresses does.
4. Tips for Using Mobile Proxies.
When using mobile proxies, keep these tips in mind to maximize your benefits and protect your online privacy:
- Follow local laws and regulations: Different countries, cities, and areas may have different rules and regulations for using proxies for surfing the internet. To prevent paying hefty fines, ensure your business complies with all the state and federal laws.
- Ensure ethical usage: As a business, you must use mobile proxies ethically. You can try to avoid activities that snatch away the rights of others or engage in malicious activities. Ethical usage of mobile proxies helps you build your reputation while ensuring a digitally safe environment for everyone.
- Adhere to the terms and services: Irrespective of the reason for using a mobile proxy, ensure you adhere to the terms and services of the website you are accessing. Failure to adhere to these terms and services may lead to unwanted legal consequences.
5. Final Words.
There’s no better solution than making mobile proxies a part-and-parcel of how you and your employees surf the internet.
Apart from protecting your company’s online privacy, these proxies play a major role in safeguarding your business’s, customer’s, and employee’s sensitive information.
Companies using the power of these proxies are more likely to navigate the digital landscape like a breeze while ensuring their data remains secure and their business operations run smoothly.
The need of the hour is staying ahead of the curve and using mobile proxies before your competitors take advantage of them!
0Comments