NAT Traversal addresses challenges posed by NAT, which disrupts direct device communications by hiding internal IP addresses behind a single public IP. It uses techniques like STUN, TURN, and ICE to establish these connections.
NAT Traversal enables services like VoIP calls, gaming, and peer-to-peer apps to work. In addition, it also allows IPSec VPNs to maintain secure tunnels across NAT devices.
Both, NAT and NAT Traversal are currently and fully reliant on IPv4 (the Internet Protocol that makes the Internet work). A workaround is to use IPv6, which offers a long-term solution because it doesn’t rely on NAT.

Table of Contents:
- The Challenges with NAT.
- What is NAT Traversal and How Does it Solve NAT Limitations?
- How Does NAT Traversal Work?
- How to Configure NAT Traversal (for IPSec)
- NAT Traversal: FAQ
- Final Words
1. The Challenges with NAT.
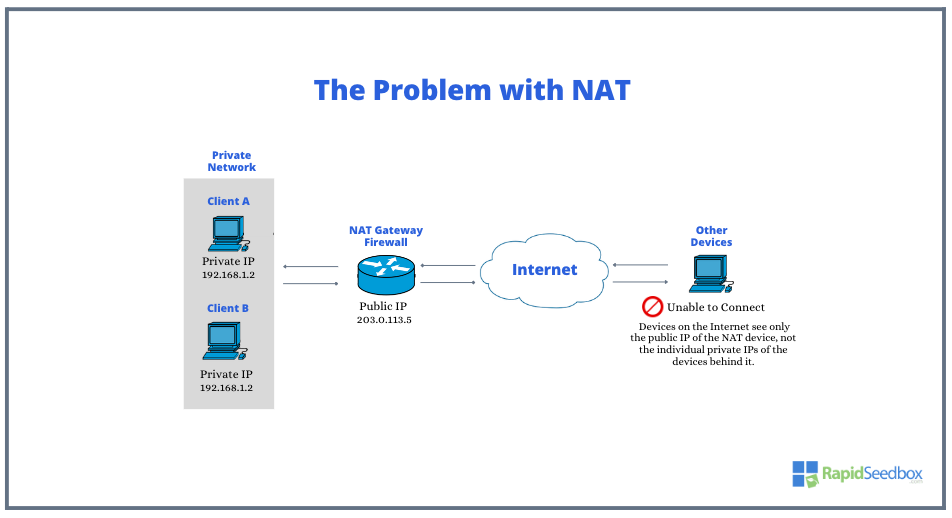
One major challenge of NAT (Network Address Translation) is that it breaks endpoint connectivity. It intercepts and modifies traffic without secure encoding and authentication, which in most cases, bypasses company security policies.
This endpoint connectivity break introduces another challenge: It hides individual IP addresses behind a single public IP. This makes it difficult for distant devices (across the internet or in different NAT environments) to try to establish direct connections with each other. It confuses routers trying to direct new connections without internal device information.
This is especially true in situations requiring peer-to-peer communication like video calls (VoIP) or online gaming.
| Note: Bear in mind that NAT comes in various forms, with completely different advantages and challenges. These include mainly Static NAT, which creates a one-to-one mapping between private and public IP addresses, and Dynamic NAT, which assigns public IPs dynamically. Other types include Port Address Translation (PAT) which allows multiple internal devices to share a single public IP, using different ports, and Overloading which is a subtype of PAT with multiple private IPs mapped to fewer public IPs. Other more uncommon types of NAT include: Twice NAT modifies both source and destination IPs, and Carrier-grade NAT (CGNAT) which is used by ISPs to map multiple private IPs to one public IP. |
2. What is NAT Traversal and how it overcomes NAT limitations?
NAT Traversal is a set of techniques that allow connections across TCP/IP or UDP protocols through NAT gateways. It solves the aforementioned NAT problem by allowing these devices to find each other and communicate with their public-facing endpoints. Its techniques can work individually or in tandem. They are ideal as workarounds for the restrictions that NAT imposes.
What techniques does NAT Traversal use?
- STUN (Session Traversal Utilities for NAT): It allows a client behind a NAT to discover its public IP address and the type of NAT it’s behind. The client sends a request to a STUN server (on the public internet,) which replies with the client’s public address and port.
- TURN (Traversal Using Relays around NAT): TURN servers act as relay points if a direct connection is impossible due to the type of NAT or firewall configurations. These servers relay traffic and maintain connections.
- ICE (Interactive Connectivity Establishment): ICE is a framework that combines STUN and TURN. It checks all possible routes to establish the most efficient connection between peers.
- UPnP (Universal Plug and Play) and NAT-PMP (NAT Port Mapping Protocol): These protocols are used to automatically configure a route through the NAT without manual port forwarding.
- IPSec NAT-T (NAT Traversal): This is a technique specific to IPSec VPN connections. NAT-T encapsulates IPSec packets in UDP to ensure compatibility with NAT.
What are the benefits of using NAT-Traversal?
As the name implies NAT traversal passes through NAT. This enables endpoints using real-time applications and services (such as VoIP, online gaming, P2P file sharing, video conferencing, instant messaging, remote desktop services, VPN, IoT devices, and more) to communicate across the Internet. Most commonly clients needing to use these applications (with high throughput and low latency) are likely restricted behind firewalls and NAT.
3. How does NAT Traversal work?
NAT Traversal starts with the typical initial NAT contact which involves creating a mapping between internal private and external public addresses/ports. For outbound connections, this is enough. For inbound connections, techniques like STUN for public IP discovery and TURN for direct communication are used. Once connections are established, NAT mappings will need to be always kept alive.
Let’s go over the STUN/TURN servers.
Let’s use the following image to explain how the technique: STUN/TURN server works.
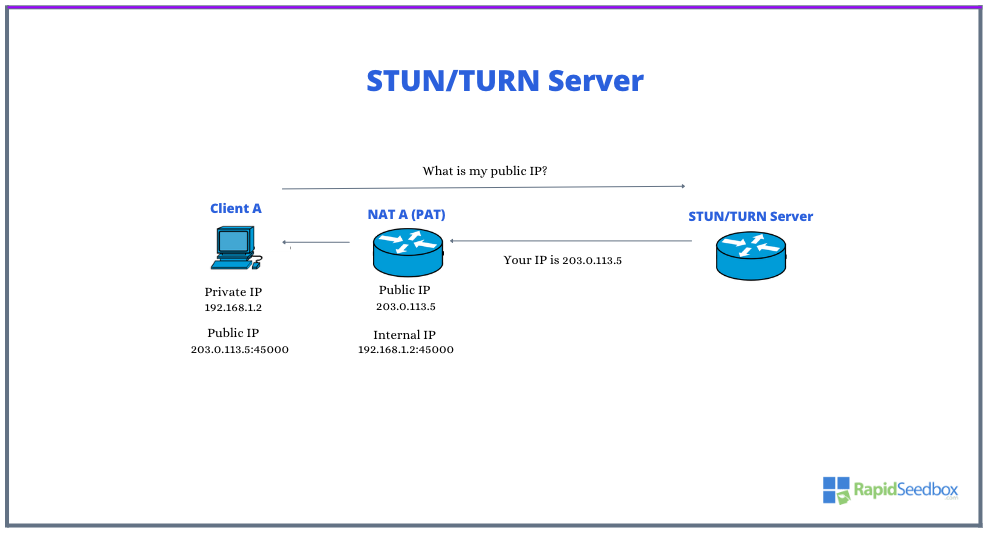
- Client A starts behind a NAT device (NAT A). It’s assigned a private IP address (192.168.1.2) that’s only valid within its local network. To establish a connection with a “remote” peer, Client A needs to know its public IP and port number. This is the unique identifier that the outside world sees, which the NAT device creates when Client A attempts to communicate with the public internet.
- Client A sends a request to the STUN/TURN Server. This server is located on the public internet and has visibility of Client A’s public IP address and port number once the request reaches it. The STUN/TURN Server then responds to Client A with the public IP address and port number assigned by NAT A (203.0.113.5:45000). This information is what Client A will provide to “remote peers” for direct communication.
- In some cases, if STUN isn’t sufficient due to the type of NAT (as discussed previously) or firewall restrictions, TURN can be very useful. TURN relays all traffic via the TURN server, acting as an intermediary for all data sent and received by Client A. The downside to TURN is, of course, its increased latency and higher bandwidth use.
Using NAT traversal to connect two distant endpoints.
Now, let’s illustrate how two endpoints (Client A) and (Client B) would connect, for example via VoIP or a File sharing P2P service, without being limited by local NAT or firewall.
Let’s go over this using the following diagram.
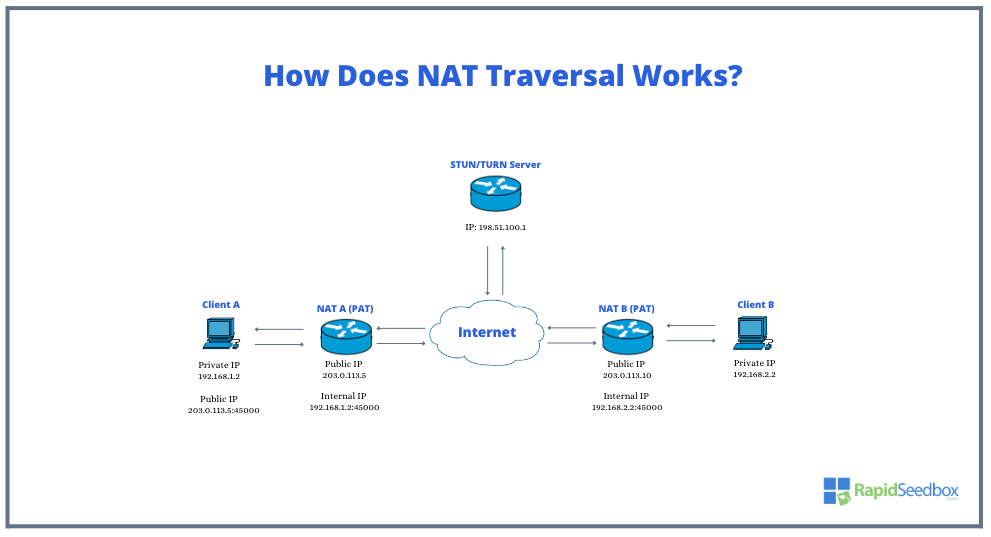
- Client A and Client B are on separate private networks, each behind its own NAT gateway (NAT A and NAT B respectively). They both have private IP addresses (192.168.1.2 and 192.168.2.2) that are only valid within their local networks.
- When Client A wants to communicate with Client B, it must go through NAT A, which assigns it a public IP address and port (203.0.113.5:45000). Similarly, NAT B assigns Client B a public IP and port for its outbound traffic.
- However, because of NAT, neither client can directly initiate a connection to the private IP of the other (192.168.1.2 or 192.168.2.2, in this case). Here, the STUN/TURN Server comes into play.
- As you already know from the previous section, Client A sends a request to the STUN/TURN Server via the Internet. The server detects the request coming from Client A’s public IP and port and responds with this information.
- Client A, now knows its public endpoint, as does Client B through a similar exchange with the server. They can now share these public endpoints with each other (often facilitated by a signaling server) to establish a direct connection.
NAT Traversal with IPSec VPN
IPSec VPNs provide secure, encrypted tunnels for data communication between different networks over the (untrusted) public Internet. Unfortunately, the IPSec protocol doesn’t inherently play well with NAT. This “incompatibility” is because IPSec encrypts packet headers which NAT devices need to read to perform their translation function. This is where NAT Traversal Over IKE (NAT-T) techniques come into play.
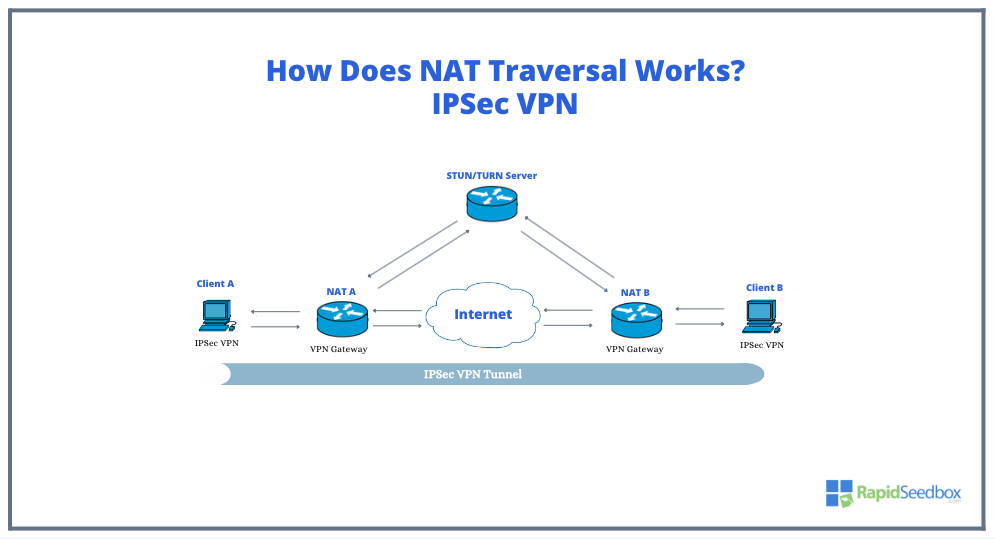
Using the image as a guide, let’s break down the NAT Traversal process in the context of an IPSec VPN:
- Clients (A and B) connect to private networks and use IPSec VPN for secure Internet communication.
- NAT A and NAT B assign public IP addresses and ports for outbound traffic, making VPN clients reachable from the outside.
- NAT-T encapsulates IPSec packets in UDP packets. This allows NAT devices to modify them.
- Technical bits: NAT-T does this by first detecting whether any NAT devices exist along the path between the IPsec peers. This is done with the Internet Key Exchange (IKE) protocol. If NAT is present, IPsec packets are then encapsulated within UDP packets, typically using UDP port 4500. This encapsulation allows the NAT device to modify only the external UDP and IP headers without affecting the encrypted IPsec content.
- Client A initiates communication with Client B, but NAT prevents direct communication. STUN/TURN Server helps clients determine public IP addresses and NAT type, which is essential for establishing IPSec VPN tunnels.
- After exchanging public IP addresses and ports, clients can create a secure IPSec VPN tunnel for data transfer.
- If there’s a NAT issue, TURN server or IKE with NAT-T support can be used to establish a VPN tunnel.
Bypass the complexities of NAT traversal today with Rapidseedbox, today!
————
4. How to Configure NAT Traversal (for IPSec).
Before diving deep into NAT traversal for IPsec configuration consider the following prerequisites: Verify your Cisco device supports IPsec and NAT traversal. Use Cisco IOS Release 12.2(13)T or later for full support. Also, ensure that other VPN endpoints and NAT devices are properly connected. This entails having a proper and operational IPSec configuration on devices, and security policies and firewall rules allowing NAT traversal traffic.
| Configuring NAT Traversal with IPSec. To use IPSec through NAT, you must allow specific protocol on firewalls. + Internet Key Exchange (IKE) over UDP port 500. + Encapsulating Security Payload (ESP) on IP protocol 50, port 4500. + For NAT-T: IPSec over UDP port 4500. + Enabling “IPsec Passthrough” on home routers often achieves these settings. |
a. Fine-tuning
Note that NAT Traversal is automatically detected and negotiated by VPN devices in Cisco IOS. There’s no need for explicit configuration steps if both VPN devices are NAT-T capable.
From the Cisco IOS device, let’s ensure NAT traversal for IPsec is activated and that its traffic can traverse through NAT devices.
- Log into your Cisco device. Enter privileged EXEC mode (via enable) and global config mode (via configure terminal).
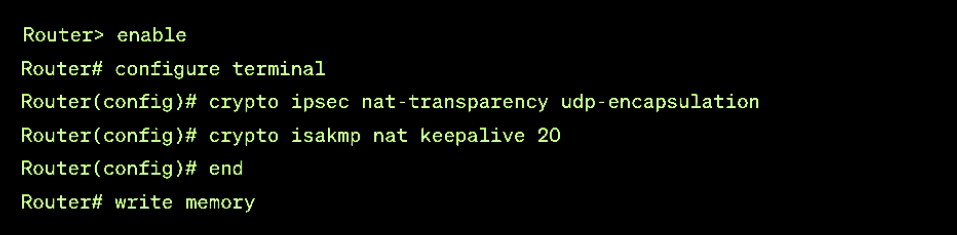
- The following Cisco IOS command enables it by allowing IPsec to encapsulate data in UDP. It makes it compatible with NAT and PAT.
- crypto ipsec nat-transparency udp-encapsulation.
- You can also fine-tune NAT traversal, by configuring NAT keepalive messages to be sent every 20 seconds to maintain the NAT mapping. NAT keepalives help maintain the NAT mapping alive during connections. Use the following command.
- crypto isakmp nat keepalive 20:
- Save and Exit. Use “end” and “write memory” commands
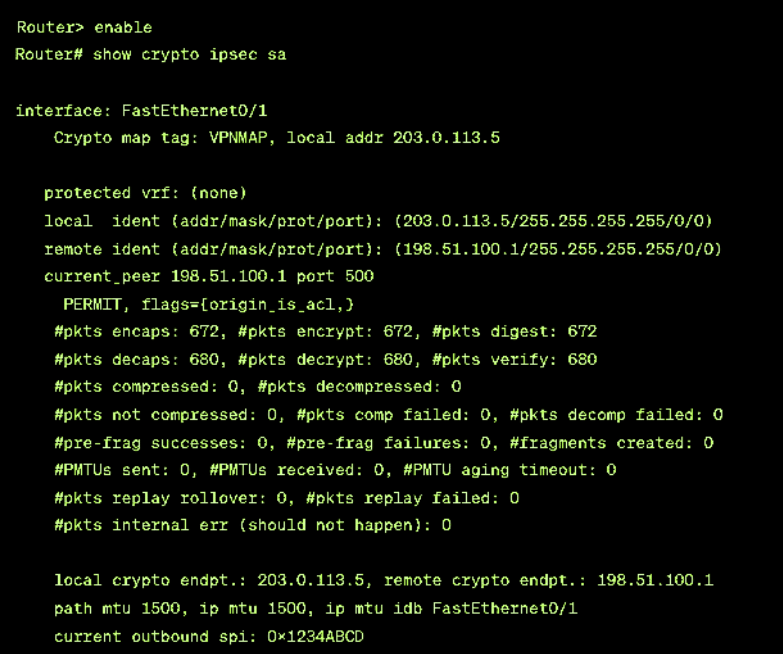
b. Verifying IPsec Configuration:
- Verify your IPsec configuration using the following command to display the settings used by current Security Associations (SAs). This command is ideal for verifying that your IPsec tunnels are established and passing traffic correctly.
- show crypto ipsec sa
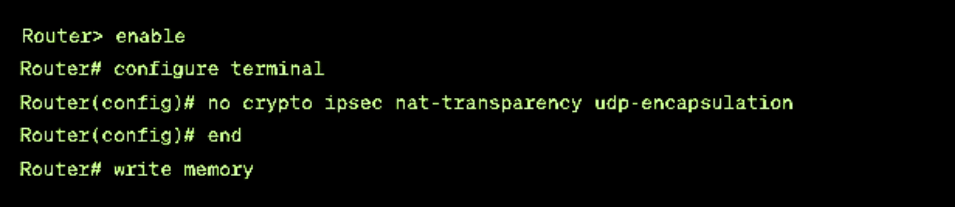
c. Disabling.
- If needed you can disable NAT traversal. This might be relevant in networks using IPsec-aware NAT. Use the following command to do this:
- no crypto ipsec nat-transparency udp-encapsulation.
| Keep the following considerations in mind: Ensure the keepalive interval is shorter than the NAT mapping expiration time to prevent disconnections. Also, be aware of potential issues like IP address mismatch due to NAT modifying source or destination addresses. |
5. NAT Traversal: FAQ.
a. What is the problem with NAT and what does NAT traversal do to solve it?
NAT acts like a kind of firewall because it obscures an internal network’s IP addresses. Although this is great for security purposes, it does pose challenges for incoming internet communications like video conferencing, online gaming, or peer-to-peer networking, which require a device to receive incoming connections from the public internet. NAT Traversal techniques allow these incoming connections from the public internet to happen.
b. What is hole punching and how does it relate to NAT traversal?
Hole punching is a NAT traversal technique. It streamlines direct communication (via a third-party server) between two endpoints behind NAT devices. This technique establishes a temporary pathway, exchanges public endpoint information, and attempts direct communication. This technique works by having each device send an outgoing packet to the other, which “punches” a hole in their respective NATs.
c. What is the purpose of NAT traversal in IPSec?
NAT traversal allows IPsec (VPN) traffic to pass through NAT or PAT devices. In other words, it resolves known incompatibilities between NAT and IPsec. NAT IPSec enables remote users to establish IPsec tunnels even when NAT or PAT is in their path.
d. What is NAT Traversal over IKE?
NAT traversal over IKE (NAT-T) is a mechanism in IPsec for encapsulating UDP packets using ESP (Encapsulating Security Payload) to better pass through firewalls and NAT. The NAT-T feature comes in Microsoft Windows XP with Service Pack 2 (but must be enabled). In addition, all major vendors (Cisco, Juniper, etc) support NAT-T for IKEv1 in their devices.
e. How IPsec and VPNs enhance security in NAT environments?
IPsec— a Cisco VPN protocol helps improve the security in NAT environments. It uses encryption, authentication, tunneling, NAT traversal, and centralized policy management to protect data. This protocol creates a secure end-to-end connection (even though NAT is there), preventing unauthorized access and even eavesdropping.
f. Is IPv6 an alternative to NAT Traversal?
IPv6 eliminates the need for NAT by providing a vast address space, allowing each device to have a unique public IP address, and by enabling direct connectivity. While IPv6 simplifies network management and supports end-to-end communication, the ongoing coexistence with IPv4 means NAT traversal is still relevant during the IPv6 migration period. Despite IPv6’s benefits, its global adoption is gradual. This means NAT traversal techniques are still needed in many current networks.
g. What is the relationship between NAT traversal techniques and firewalls?
NAT traversal techniques enable connections through NAT devices. But these can also include NAT devices with firewall functionalities. Firewalls do complicate NAT traversal because they can block incoming connections or outbound traffic on certain ports. To make NAT traversal techniques work with the firewall, it needs to be compatible with the firewall rules.
h. NAT Traversal vs Port forwarding: What are their differences?
NAT traversal and port forwarding can both manage NAT limitations, but they do it differently. On the one hand, as you already know, NAT traversal establishes device-to-device connections without manual configuration changes. Port forwarding, on the other hand, is a manual configuration on a NAT device that allows external devices to initiate connections to a specific internal device. NAT traversal is automated and dynamic while port forwarding requires explicit manual configuration.
6. Final Words.
NAT Traversal ensures that devices behind NAT can talk to each other without any problems. It’s key for applications like voice calls over the internet (VoIP), gaming, and sharing files (P2P). The tricky part is that NAT makes it difficult for devices to find and connect because it changes how traffic flows and hides their real IP addresses. To get around this, we use NAT traversal techniques like STUN, TURN, and ICE. For secure connections over IPsec VPNs, we have NAT-T, which encapsulates IPsec packets in UDP so they can pass through NAT without any problems.
But, as networks change and more people start using IPv6, NAT Traversal might not be as important as it is now. Until then, though, learning how to use NAT Traversal to make sure that your real-time apps and services work smoothly and safely is key.
0Comments