Are you curious about learning what is HTTP proxy and its inner workings? About its significance in today’s online communications? Do you want to know how an HTTP proxy can help with your privacy, security, and performance while visiting certain websites?
Look no further! In this article, we will unravel the concept of HTTP proxies, delving into their definition, types, and how they work. We will uncover the numerous benefits they offer, as well as the limitations to be aware of. Additionally, we will guide you through the process of configuring an HTTP proxy, ensuring you can harness its power effectively.
Without further ado, let’s learn what is an HTTP proxy.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents.
- What is HTTP Proxy?
- Types of HTTP proxies.
- How HTTP Proxy Works.
- HTTP Proxy Benefits.
- HTTP Proxy Limitations.
- How to Configure an HTTP Proxy?
- HTTP Proxy: FAQ.
- Conclusions.
1. What is HTTP Proxy?
The HTTP (HyperText Transfer Protocol) is the foundation of most communications happening on the Web. It helps with the exchange of information between HTTP clients (i.e. web browsers or mobile apps) and HTTP servers (i.e. Apache HTTP server, Nginx, IIS, etc).
The HTTP proxy is a type of server sitting between HTTP clients and servers. It intercepts HTTP traffic and forwards HTTP requests and responses. This proxying of HTTP traffic is useful for managing and controlling HTTP traffic. Additionally, HTTP proxies can also provide anonymity (for both HTTP clients and servers).
2. How HTTP Proxy Works.
By delving into the inner workings of HTTP proxies we can gain insights into how these servers intercept requests, mask IP addresses, and implement filtering and blocking mechanisms. In this section, we will explore the step-by-step process of how HTTP proxy works. We’ll discuss the mechanisms that enable these servers to enhance security and privacy and control web communications.
The Client, the Proxy, and the Server.
There are three players with different roles: the HTTP Client, the HTTP Proxy Server, and the HTTP Destination Server. Each of these components plays a crucial role in the secure transmission of data over the web.
Refer to the flowchart picture below.
- HTTP Client: Typically a web browser or an application that initiates an HTTP request for a resource from a web ‘destination’ server.
- HTTP Proxy Server: This component acts as a bridge between the HTTP client and the destination server. It has the capability to intercept all communications.
- HTTP Destination Server: The HTTP destination server is the web server that hosts the requested resource.
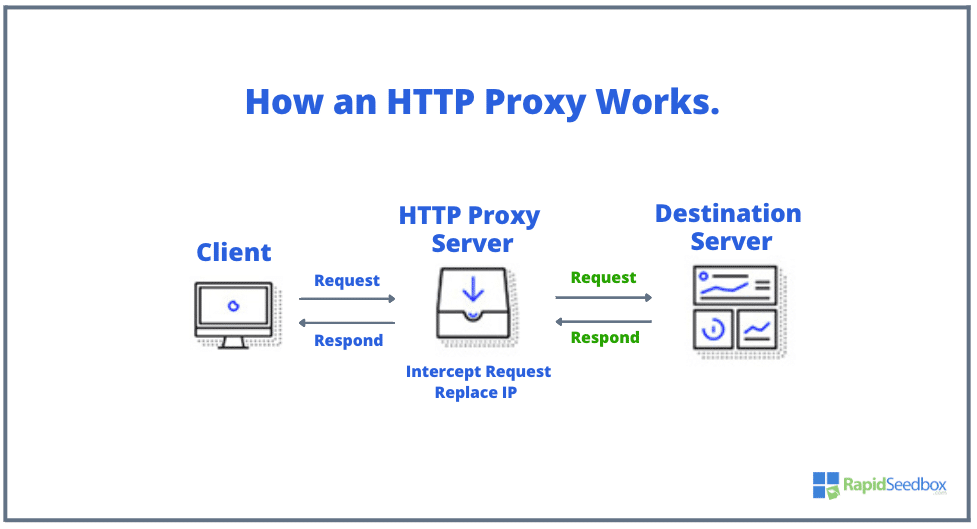
Here is the flowchart of how each of these components interacts with each other in different scenarios.
a. Request interception and forwarding:
- Step 1: The client sends an HTTP request to access a website (at the destination server).
- Step 2: The HTTP proxy server intercepts the request that the client generated initially.
- Step 3: The proxy server evaluates the request, checks its policies, and determines whether to forward the request or block it.
b. [Optional] IP address masking:
Depending on its anonymity level, HTTP proxies can modify or delete certain “communication headers” to allow anonymity. These headers include the X-Forwarded-For (contains the client’s IP address), Via, Forwarded, X-Forwarded-Host, and X-Forwarded-Proto. The IP Address masking happens only if, the HTTP proxy server is configured to change X-Forwarded-For packet headers.
- Step 4: If the request is allowed, the proxy server replaces the client’s IP address with its own IP address in the outgoing request.
- Step 5: The proxy server sends the modified request (green in the picture) to the destination server on behalf of the client.
- Step 6: The destination server receives the request and responds (green in the picture) to the proxy server.
c. Filtering and blocking:
- Step 7: If the proxy server forwarded the request to the destination server, it will wait for, and receive the response from the destination server.
- Step 8: The proxy server can now simply forward the response to the client, or apply various filtering and blocking mechanisms based on its configured policies.
- Step 9: If the response passes the filtering criteria, the proxy server forwards it back to the client.
- Step 10: The client receives the response as if it came directly from the destination server.
3. Types of HTTP proxies
There are many different types of proxies, but generally, when it comes to the functionality of HTTP, we can consider either forward proxies or reverse proxies (along with their anonymity level).
a. Forwarding HTTP Proxy:
A forwarding proxy, also known as a forward proxy or gateway, is a type of server sitting between the client and the server. When a forwarding proxy receives HTTP requests from the client, it forwards them to the destination server (most likely a website) on behalf of the client. Forwarding proxies are commonly used to control and manage outgoing traffic from a network, reducing bandwidth usage and providing anonymity to users.
A “Forwarding” HTTP proxy can be further classified based on anonymity level. They can be either Transparent Proxy (Level 3), Anonymous Proxy (Level 2), or Elite or High-Anonymity Proxy (Level 1).
b. Reverse HTTP Proxy:
Just like a forwarding proxy, a reverse HTTP proxy also acts as an intermediary between the client and the servers. But unlike a forwarding proxy that handles client requests and forwards them to servers, a reverse proxy manages incoming requests from clients. A reverse HTTP proxy is designed to sit in front of web servers.
When a ‘remote’ HTTP client sends a request, the reverse proxy forwards it to the appropriate HTTP server based on various criteria such as load balancing or content caching. The “Reverse” HTTP proxy can also be further classified based on anonymity level. They can be either Transparent (Level 3), Anonymous (Level 2), or High-Anonymity Proxy (Level 1).
4. HTTP Proxy Benefits.
The most significant benefit of forwarding HTTP proxies is that they provide anonymous browsing activity. With it, users can hide their IP addresses, and thus protect their online identity or access limited (or prohibited) websites. In addition, forwarding HTTP proxies can also help filter incoming traffic to protect internal networks. Such capabilities can also be useful for providing caching, filtering, and authentication services. Saving large amounts of bandwidth in internal networks and protecting remote networks.
Reverse HTTP proxies are explicitly designed to enhance the security, scalability, and performance of HTTP Servers (websites, apps, and services). They can help in distributing incoming traffic among multiple servers (with load balancing, caching, and content optimization) helping reduce the impact of traffic spikes or the feared DDoS attacks. These reverse HTTP proxies also provide additional layers of protection by hiding the true identities of web HTTP servers.
Summary of Proxy Benefits
- Security and Privacy Enhancement: Both reverse and forwarding HTTP proxies can intercept and filter requests and responses. They can protect sensitive information from potential threats. HTTP proxies improve the security of either HTTP clients or servers.
- Anonymous Browsing: HTTP proxies allow users to hide their IP addresses. They anonymize the client’s identity by masking their IP address, making it harder for malicious actors or third-party surveillance attempts to track their online activities.
- Access to Geographically Restricted Content: An HTTP proxy allows users to access geographically restricted content. By routing the requests through a proxy server located in a different geography, users can bypass local restrictions and access websites, services, or content.
- Enhanced Performance and Caching: HTTP proxies can significantly improve browsing speed and performance by caching frequently accessed web content. This proxy caching mechanism leads to a more efficient browsing experience.
- Content Filtering and Compression: The HTTP proxy server examines web traffic and performs content filtering to identify and mitigate potential security risks. This feature enables the detection of suspicious content, such as viruses or intrusions, or advertisements removal. Additionally, the HTTP proxy may also help accelerate requests from an HTTP destination by (compressing) reducing the data size.
5. HTTP Proxy Limitations
Although an HTTP proxy can provide a great deal of benefits, it is also worth considering the following drawbacks. Knowing the following HTTP proxy limitations beforehand can help you evaluate your specific requirements and risks before implementing this server.
- HTTP is not HTTPS: HTTP proxies are not designed to forward secure HTTPS data. This would otherwise break the chain of trust between the HTTPS client and server. HTTPS data transmitted through a forward HTTP proxy would not be secure, as it would require decryption and re-encryption using local or self-signed certificates. For this, there are HTTPS proxy servers that can encrypt and decrypt HTTPS traffic. But they need to be fully trusted, as you would need to use their local or self-signed certificate.
Note: It is possible to have HTTPS connections over proxy servers. The method involves using the CONNECT command to establish a secure communication channel between the client and the server through the proxy. This allows for the secure transmission of data while preserving the end-to-end security provided by SSL/TLS. However, keep in mind that not all proxy servers support this feature, and some may require specific configurations or protocols such as SOCKS.
- Plain text transmission: HTTP proxies are designed to transmit data in plain text, which means that sensitive information can be intercepted and read by unauthorized parties (including the HTTP proxy manager).
- Data caching limitations: While data caching can improve performance, it can also pose risks if the cache is compromised. A hacked cache data including users’ data and login credentials, may lead to potential misuse.
- Compatibility and configuration issues: HTTP proxies may have compatibility and configuration challenges when used in conjunction with local networks. Different network parameters between the proxy and the local network can cause issues that need to be addressed and configured properly.
6. How to Configure an HTTP Proxy?
In this section, we will go through a step-by-step guide on how to configure an HTTP proxy on different devices and browsers. It’s important to note that the specific steps for configuring an HTTP proxy may vary depending on the device, operating system, and browser. It is also important to know that you can also use HTTP proxies on different types of software, like torrent clients, streaming platforms, video games, etc.
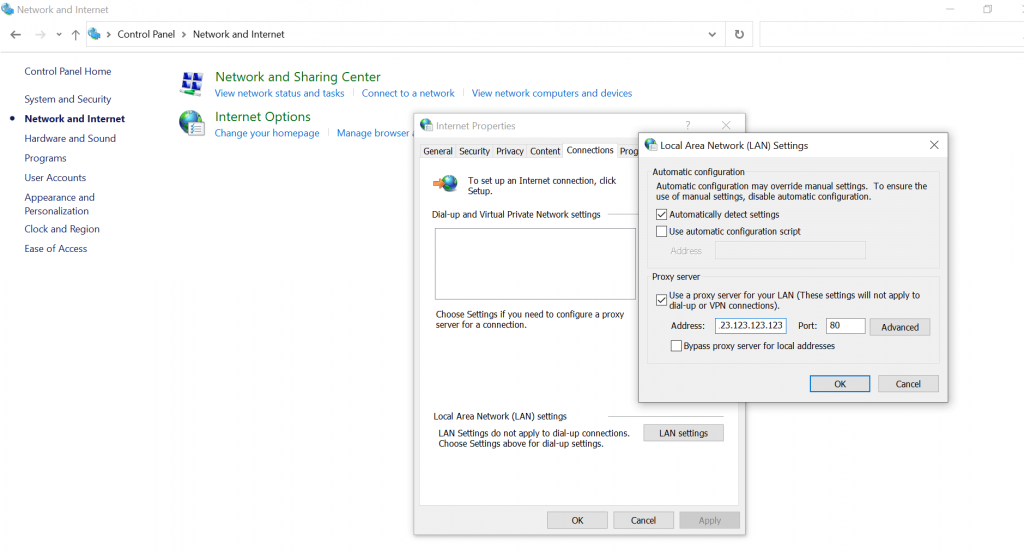
a. Configure proxy settings in Windows:
The following step-by-step guide to configuring an HTTP proxy server on Windows might not be applicable to all Windows versions. The naming and location of configurations and settings will vary from Windows version to version.
- Open the “Control Panel” > Click on the “Network and Internet” tab > then “Internet Options” > then go to the “Connections” tab and then click on the “LAN settings” button.
- In the LAN settings window, check the box for “Use a proxy server for your LAN.”
- Enter the IP address or hostname of the HTTP proxy server in the “Address” field.
- Enter the port number associated with the HTTP proxy server in the “Port” field (i.e. 80 or 8080).
- Click “OK” to save the changes and close the window tab. The HTTP proxy should now be configured on your Windows device.
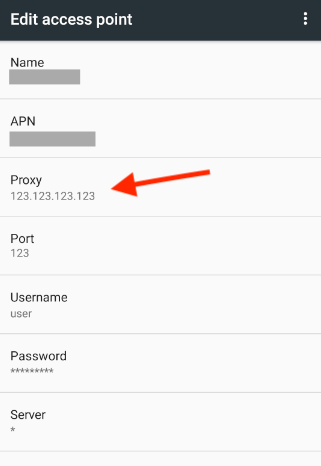
b. Configuring an HTTP proxy on Android.
Android devices allow proxy configuration via manual or PAC (Proxy Auto-Config) Mode. In manual mode, you can manually enter the proxy settings on your Android device, which is easier to configure if you have all the proxy information. On the other hand, to use PAC mode you’ll use a Proxy Auto-Config file hosted on a server. The PAC file contains JavaScript functions that determine which requests should be routed through the proxy.
- Open the “Settings” app on your Android device. Scroll down and tap on the “Network & Internet” option. Tap on “Wi-Fi” or “Mobile network,” depending on which connection will forward its traffic to the HTTP proxy.
- For Mobile Network > on Mobile Networks > tap on Advanced > Edit APNs > Choose the APN you are using > Edit Access Point Network > Edit proxy settings.
- For Wi-Fi Networks > Tap on Settings > “Network & Internet” > “Internet” option to see available network connections.
- If you’re already connected to the network, tap on the network on the Internet page. If it’s a saved network, tap and hold the name of the network and select “Modify”.
- On Network Details > tap on the “Edit” button in the top-right corner.
- In the Advanced options, locate the Proxy section and tap on the default value, “None”.
- Choose either “Manual” or “Proxy Auto-Config (PAC)” from the drop-down menu.
- If you choose “Manual”, enter the proxy hostname or IP address and the port number. You can also bypass the proxy for specific websites.
c. Using browser extensions for proxy configuration:
- Install a browser extension that provides proxy functionality, such as FoxyProxy for Firefox or Proxy SwitchyOmega for Chrome.
- Once installed, click on the extension icon in your browser’s toolbar (1). In the extension settings tab, you’ll locate the proxy configuration options (2).
- Enter the IP address or hostname of the HTTP proxy server in the appropriate field.
- Enter the port number associated with the HTTP proxy server. 8080 is the default port.
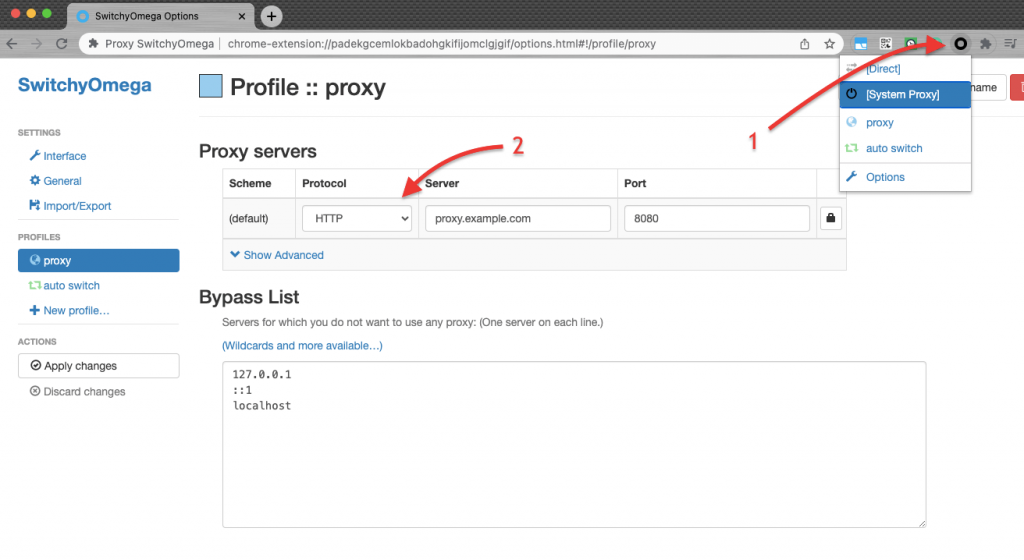
- Save the settings and enable the proxy within the browser extension.
- The proxy should now be configured and active for your browser.
7. HTTP Proxy: Frequently Asked Questions
a. What is the difference between an HTTP proxy and an HTTP tunnel?
An HTTP proxy server acts as an intermediary between a client and a server. On the other hand, an HTTP tunnel is a technique for encapsulating lower-level protocols within the HTTP protocol to bypass network restrictions. HTTP tunneling is achieved through the CONNECT method, allowing data to be securely transmitted across networks. The proxy server focuses on managing and forwarding requests, while the tunnel focuses on creating a secure pathway for data transmission.
b. VPN vs Proxy: What are their differences?
A VPN (Virtual Private Network) creates a secure and encrypted connection (tunnel) between your device and the internet. The VPN provides privacy and security by routing all your internet traffic through a VPN server. A proxy server, on the other hand, acts as an intermediary between your device and the internet. Proxies do not encrypt traffic, they only modify packet headers to mask IP addresses. This masking provides anonymity and bypasses IP-based restrictions. To know all of their differences, check the VPN vs proxy full article
c. Can I perform web scraping with an HTTP proxy?
Yes, you can perform web scraping with an HTTP proxy server to collect data from websites. The proxy server helps in hiding the identity of the scraper and allows them to access websites without being blocked or detected.
d. Can I use an HTTP proxy to access YouTube?
Yes, an HTTP proxy can be used to access YouTube. By routing your YouTube requests through an HTTP proxy server, you can bypass any restrictions or blocks imposed on accessing YouTube in your region or network.
e. What is a PAC file?
Proxy Auto-Configuration (PAC) files (written in JavaScript) determine whether browser requests should be forwarded to a proxy server or sent directly to the destination. Additionally, PAC files provide automatic and dynamic proxy configuration based on predefined rules.
f. Can I use an HTTP proxy with blockchain technology?
Yes, an HTTP proxy can be used with blockchain technology. Such servers can offer benefits such as online security, anonymity, and unblocking crypto exchange websites, making them valuable tools for cryptocurrency users.
g. Do HTTP proxies log data?
Yes HTTP proxies have the capability to log data. They can record and analyze the activity and traffic passing through an HTTP proxy server. HTTP logging allows administrators to monitor and analyze user behavior, detect potential security threats, and troubleshoot network issues.
h. TOR vs HTTP Proxy: What are the differences?
TOR and HTTP proxy are both online privacy and security technologies. However, TOR is a network of volunteer-operated servers that encrypt and route internet traffic through multiple relays. An HTTP proxy, on the other hand, is an intermediary server between a client and a server, primarily for filtering, caching, or masking IP addresses.
i. SOCKS5 Proxy vs HTTP proxy?
HTTP and SOCKS5 proxy are both proxy protocols but differ in their functionality. SOCKS5 is a more versatile protocol that supports various types of traffic, including TCP and UDP, making it more suitable for applications such as torrenting, VoIP, gaming, etc. HTTP proxy, on the other hand, is specifically designed for handling HTTP traffic.
j. What are the differences between free and paid proxies?
Free proxies are available at no cost. You can find tons of free HTTP proxies online. They provide basic functionality for IP address masking and accessing blocked content. However, it is important to know that free proxies have lots of limitations in terms of speed, reliability, and security. Paid proxies, on the other hand, require a subscription and offer better performance, reliability, and security. They may provide dedicated IP addresses, stronger encryption, and customer support.
8. Conclusion
HTTP proxies serve as indispensable intermediaries between HTTP clients such as web browsers and HTTP servers like web servers. HTTP proxy servers act as gatekeepers. They safeguard sensitive information and enhance privacy. In addition, HTTP proxies also enable content caching and load balancing, resulting in improved performance and reduced bandwidth usage. Although HTTP proxies provide such fantastic benefits, they also come with a few limitations that you should keep in mind, these include potential bottlenecks and compatibility issues with certain applications.
By configuring an HTTP proxy properly, you can enjoy its advantages while mitigating its drawbacks. If you have any questions about HTTP, please check our FAQ section or leave your question in the comment section below!
0Comments