VPN vs. Proxy. Which one is better? It depends on you.
Although VPNs and proxies may seem similar on the surface, as they both provide Internet security and privacy, underneath, they are two completely different creatures— born and raised to provide different solutions.
VPNs were designed to “virtually” link two geographically distant computers or networks using risky networks such as the Internet. Conversely, proxies were designed to add structure to complex distributed networks by centralizing all requests and responses. Therefore, both solutions provide different levels of privacy and security as byproducts.
In this article, you’ll learn the top 6 key differences between VPN vs. Proxy. You’ll also learn when to use one as an alternative to the other.
Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents.
- What is a VPN?
- How does a VPN work?
- When should you use a VPN?
- What is a Proxy Server?
- How does a proxy work?
- When should you use a proxy?
- VPN vs Proxy: Top 6 Differences.
- Paid vs Free.
- VPNs hide all traffic, but proxies provide more flexibility.
- VPNs provide end-to-end encryption.
- Speed and User Experience.
- Fast Torrenting vs Security.
- Price.
- Final Words.
What is a VPN?
A Virtual Private Network (VPN) is a group of virtually interconnected clients and servers. As mentioned earlier, VPNs were designed to extend local networks geographically. Since VPNs don’t rely on physically connected systems, their networks can span worldwide.
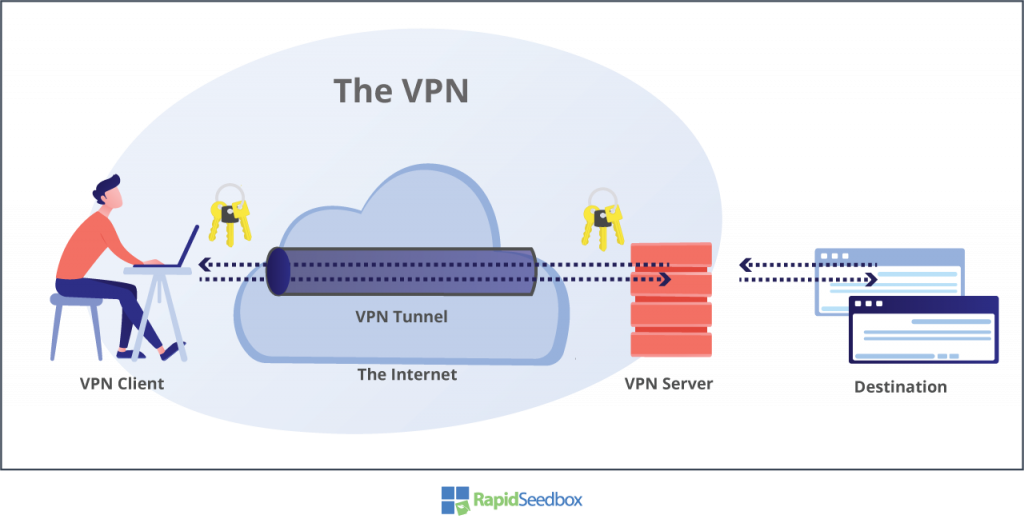
A VPN typically uses the Internet as a medium. VPN clients and servers use the grid (the Internet) to exchange packets, and to keep it secure, they create a kind of “secret underground” tunnel. Nobody with access to “this grid” (ISP, hackers, government, etc.) would be able to tell what is going on and through those VPN tunnels.
a. How does a VPN work?
To establish these hidden tunnels, VPNs use encryption. Both the client and server agree and share a set of encryption-decryption keys for creating this tunnel.
Let’s say you are connected to a VPN server and want to browse the Internet. The following is the message flow that illustrates a standard VPN client-server connection.
- Before your Internet request for a service (i.e., HTTP or P2P) goes out, the client’s VPN process takes control.
- The VPN client encrypts the IP packet’s data using the public key received from the server and then encapsulates the request with the new destination IP: the VPN server.
- The client transmits the encrypted packet across the Internet towards the VPN server.
- Anyone across this path, either a coffee shop hacker, ISP, government, or your neighbor, would still be able to capture your packets but never to make sense out of your data.
- The VPN server receives, opens, and decrypts the packet using the private key.
- The VPN server decapsulates the original client’s packet, then forwards the original request using the server’s VPN IP to the intended destination (for example, youtube.com or facebook.com).
b. When Should you use a VPN?
Widespread use cases are (but are not limited to): Extending private networks, circumventing geographical restrictions, bypassing censorship, protecting true identity, improving branch-headquarters security, adding security when using public networks, and more.
- Singular end-users or small businesses should use a VPN to: Protect privacy and anonymity while doing non-resource intensive activities like web browsing.
- Mid-large companies should use VPNs to extend networks geographically or connect to distant networks over the Internet. VPNs can allow mobile and remote users secure access to the business’s internal network. VPNs are also great tools for testing geo-tailored apps and content from the point of view of different audiences.
What is a Proxy Server?
As mentioned before, proxies were designed to add structure to complex distributed networks by centralizing all their requests and responses. To do this, they act as intermediary nodes between clients, servers, networks, or the Internet.
Proxies are like security lobbies. When you go into a building, security lobbies might have some regulations like requesting your documents, scanning your bags, monitoring fever, etc. There’s no way to enter or exit the building without going through this lobby.
A proxy is similar because when you go (request services) inside a network or outside (Internet), you’ll have to go through the proxy— which would generally inspect, stop, or modify your requests.
a. How does proxy work?
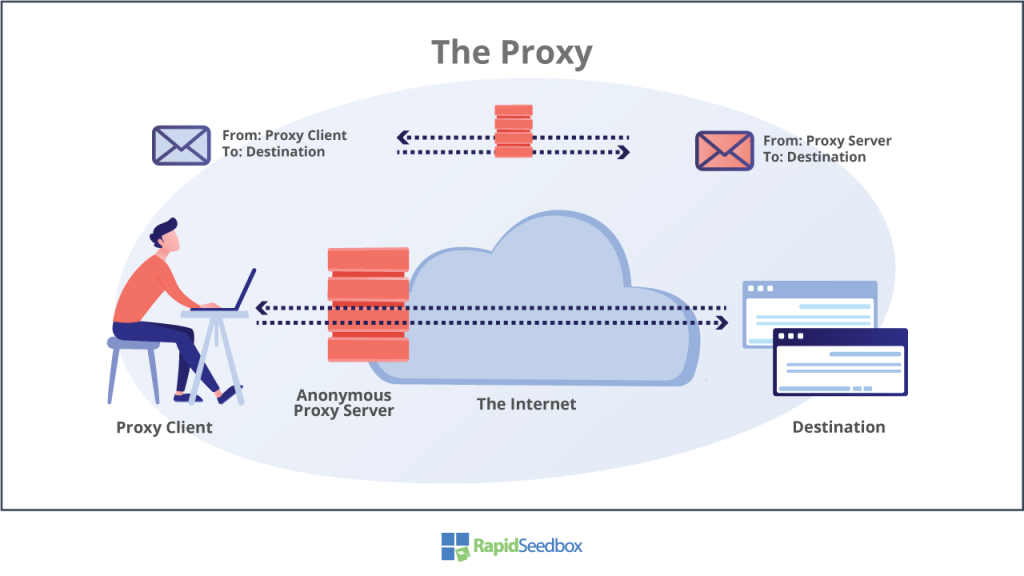
Types of proxy come in different colors and flavors, where each would work entirely differently. But generally, being intermediaries to requests and responses proxies have the following message flow. Let’s say you are connected to the Internet via an anonymous web proxy.
- You have a web proxy server (HTTP) configured on your computer.
- Your web browser will forward all HTTP requests to this proxy’s IP.
- The proxy, located anywhere, from within your network to across the world, receives your request. Anyone across this path will be able to capture your packets and read unencrypted messages.
- The anonymous proxy will modify the source IP so that the destination can’t recognize the true source of traffic.
- The proxy server forwards the client’s request to the destination.
NOTE: Proxies were initially designed to be deployed at the internal network’s perimeter— facing the Internet. These Internet-facing proxies provide the network administrator, full control over what external resources the internal users can access (similar to a firewall). But in reality, a proxy can be located anywhere in the world and still serve its purpose.
b. When should you use a Proxy?
- Personal or small businesses should use a proxy if they are looking for the right balance between anonymity and speed. Proxies are popular for bypassing geo-restricted content and censorship. In addition, a proxy server like SOCKS5 can provide faster and better performance for services like streaming, video gaming, and P2P, and it can also provide authentication for added security.
- Mid to large companies should use a proxy: to monitor and filter incoming/outgoing traffic, web scraping, ad verification, SEO, website testing, geo-tailoring, threat hunt, and more. Nowadays, a widespread use case is the globally distributed network of proxy servers deployed across multiple geographical areas. This network of proxies provide buffering, caching, and even to help absorb volumetric attacks, like DDoS. This is known as a CDN (Content Distribution Network).
VPN vs Proxy: Top 6 Differences.
1. Paid vs. Free.
The differences between one technology and the other are always bolder when a service is, paid vs. free. When a VPN or proxy is free, there has to be a way for the provider to sustain their proxy or VPN business. Both VPNs and proxies require resources, infrastructure, and maintenance and monitoring personnel. So, if you are using a free VPN or a free and open proxy, you’ll likely face privacy and security issues at some point.
VPNs require more resources which is probably, why you don’t see many free VPNs out there. But still, free VPNs can be used to make a profit. They are often used to collect data from users, killing the whole purpose of “Internet privacy.” Such free VPNs make money, not from end-users but from selling data (traffic logs) to marketing and advertising agencies. Even commercial VPNs with headquarters in countries with strict data regulations (Five Eyes Alliance) may leak data. They are required to keep logs. So, anytime the government or other agencies come with a warrant, the VPN provider will need to turn in the stored data logs.
Since a proxy requires less infrastructure to deploy (no encryption), there are generally more available “free, open, and insecure proxies” out there.
2. VPNs hide all traffic, but proxies provide more flexibility.
A significant difference between Proxies and VPNs is that both operate at different layers of the OSI model. The popular VPN protocols like PPTP, L2TPv3, and IPSEC operate at layer 3 (network layer). Of course, VPN uses layer 4 to establish communications. For example, PPTP uses TCP (layer 4), while L2TP and IPSEC use TCP and UDP (Layer 4) to establish the tunnel. But once a VPN tunnel has been established, VPN protocols operate just like network interfaces. This operation at layer 3 means a VPN takes your full traffic (DNS, HTTP, P2P, VoIP, etc.), regardless of port number or application, and encrypts it.
Proxies, on the other hand, work at layer 7 (application layer), with the exception of the SOCK5 proxy, which operates at layer 5. Operating at layers 5-7 provides much more flexibility to how you selectively route your traffic. For example, you could have only HTTP (web browsing) going through a proxy, while the rest of Internet traffic (DNS, SMTP, FTP, etc.) uses the normal network interface.
3. VPNs provide end-to-end encryption.
Encryption is the method of converting human-readable text into incoherent and random ciphertext data. To ensure a recipient understands this ciphertext data, both the sender and recipient must agree on a set of cryptographic keys.
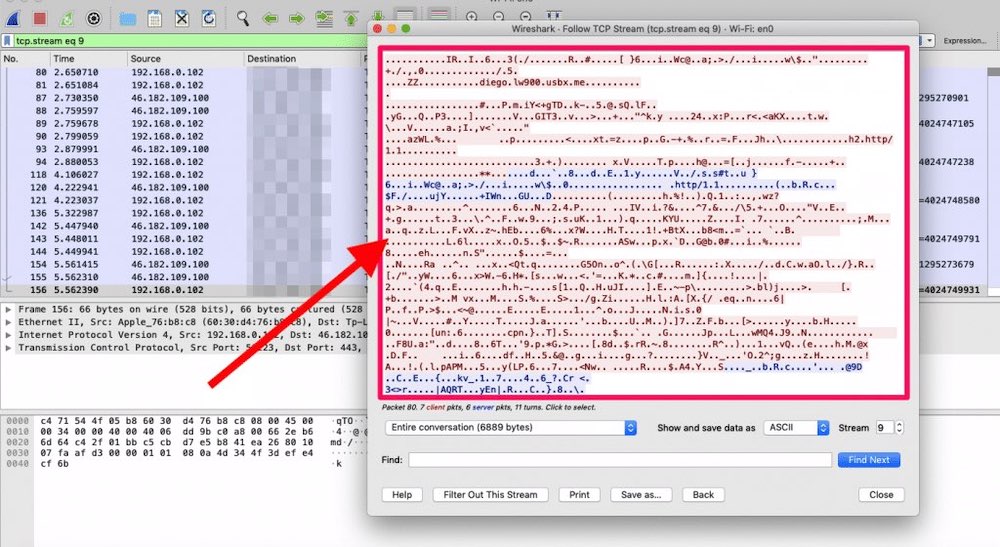
Encryption is what sets VPNs apart. It improves the level of security and privacy, exponentially. Although a hacker, ISP, or government could still intercept and capture your traffic traveling through the VPN encrypted tunnel, they wouldn’t be able to make sense of this ciphertext data, which looks like this (refer to the screenshot below).
The level of privacy in a VPN depends on the cryptographic power of the encryption mechanism. There are various encryption algorithms, some weaker, and easier to break, while others are stronger, unbreakable, and even used by the military and NSA. Encryption algorithms dictate how data is hidden in a message; examples are 3DES, AES, and RSA. These mechanisms use a set of keys and ciphers (128 or 256 bits) to hide information and are used by various security protocols. Examples of VPN encryption protocols are PPTP, L2TP, SSTP, IKEv2, OpenVPN, IPSec, WireGuard, and more.
Proxy servers, on the other hand, are not designed to encrypt data. By concept, proxies mask your IP with theirs but do not encrypt data. You could use proxies with SSL to make up for that lack of encryption, but this workaround requires technical expertise.
4. Speed and user experience.
Since proxies were created for a completely different purpose: “to centralize and simplify distributed network’s requests,” their security mechanisms are entirely different from those of VPNs.
Proxies don’t have that encryption overhead, so they are usually faster than VPNs. Although browsing the Internet with a VPN might not affect your user experience, it is the traffic with the highest load like streaming video, P2P file transfers, or gaming that does.
The fastest kind of proxy is a simple tunneling proxy or, in other words, your everyday “Internet Gateway.” This kind of proxy doesn’t modify requests and responses (it just centralizes and forwards them). Other types of proxies such as anonymous proxies, DO change requests, and responses. These proxies mask (hide) the original request of the source to the destination resource. Some proxy services may even employ caching systems for faster website load times and retrievals.
5. Fast Torrenting vs. Security.
VPN vs proxy for torrenting? These two technologies provide a different speed, performance, and security when it comes to torrenting. In a VPN scenario, since all outgoing data needs to be encrypted by the VPN client, the speed and performance while torrenting will be degraded. Removing that encryption overhead makes all the difference for speed but the tradeoff is security and privacy.
- Your ISP and government? If your ISP or government inspects your traffic at layers 4 or 7, they could identify a P2P port or application. A VPN would encrypt your entire traffic from layers 3 to above, including P2P information. A proxy, on the other hand, does not hide ports and applications, meaning that ISP and governments could intercept and detect such traffic.
- At the torrent swarm? Both VPN and the Proxy server will use their IPs and not yours to participate within a torrent swarm. Except with transparent and tunneling proxies, as they do not mask your IP with theirs.
6. Price.
As stated in the first “proxy vs. VPN difference”, how you get your hands on either a VPN or proxy makes all the difference. Prices for VPNs and proxies are slightly different. Although you can find cheap VPNs for shared resources and even free (in some cases), the price for a business VPN tends to scale in the long run. Supporting a VPN for a large business would require more infrastructure, support, maintenance, and monitoring.
Paid proxies can be much cheaper than paid VPNs. Especially IPv6 proxies, as you can obtain hundreds or thousands of proxies (fresh IPs) at a good price.
Final Words.
VPN vs Proxy? Which one is better? What are their main differences?
- The differences between a VPN vs proxy will be most noticeable when you go either for a free vs. paid service. For example, your privacy and security will be highly considered when using a premium proxy, and it will be almost ignored with a free VPN service (and vice versa).
- VPNs do stand out in the area of security due to the encryption mechanisms they use to scramble and hide data. So this will save you from exposing sensitive data while connecting your computer via risky networks like public WiFis and getting hacked. But still, under the right conditions, a premium proxy service can be as private as a paid VPN service. As long as proxy resources are not shared, and the user uses a dedicated SOCKS5 proxy server and is connected via tunneling like SSH, a proxy server can be as secured as a VPN.
- Overall, it comes down to your particular use case and what you are willing to spend. For example, VPNs can be great for web browsing but can degrade your speed and experience for traffic-intensive applications like torrent and streaming media. On the other hand, since proxies don’t deal with encryption overhead, their speed and performance tend to be better for particular applications like torrenting, streaming, web scraping, SEO, circumventing censorship geo-restrictions, etc.
Get your hands on premium high-performance IPv6 proxy today and try it for free for 14 days.
Free Vectors used from Freepik
0Comments