Open proxies offer a gateway to anonymous browsing and unrestricted content access. But is this open gateway, safe for you and provides you with the best experience?
This article dives into how an open proxy works, its benefits, and risks, and provides insights into managing and utilizing them effectively.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute an endorsement of any activities (including illegal activities), products, or services. You are solely responsible for complying with the applicable laws, including intellectual property laws when using our services or relying on any information herein. We do not accept any liability for damage arising from using our services or information contained herein in any manner whatsoever except where explicitly required by law.
Table of Contents
- What is an Open Proxy and How It Works?
- Comparison Table: Pros and Cons of Open Proxies
- Open Proxies: Use Cases
- Closed Proxies vs Open Proxies
- Open Proxy Lists Providers and Tools
- FAQ on Open Proxies
1. What is an open proxy and how it works?
An open proxy is a type of proxy server that is accessible by any Internet user without requiring authentication. It acts as an intermediary between a user’s device and the internet, allowing users to conceal their IP address and location. Open proxies are commonly used for anonymous web browsing and accessing geographically restricted content. They can be provided (as with any type of proxy) thorugh a global network of proxies, at different anonimity levels (transparent, Anonymous, and elite), or through different protcols (SOCKS5 or HTTP proxies)
How Does It Work?
An open proxy server acts as a pivotal middle-man that ensures requests and its subsequent responses are routed without direct linkage to a device. In other words, an open proxy forwards users’ requests to the internet, hiding their IP addresses. Requested data is sent back to the user through the proxy server, providing anonymity. The picture below shows this simple concept (in a visual representation):
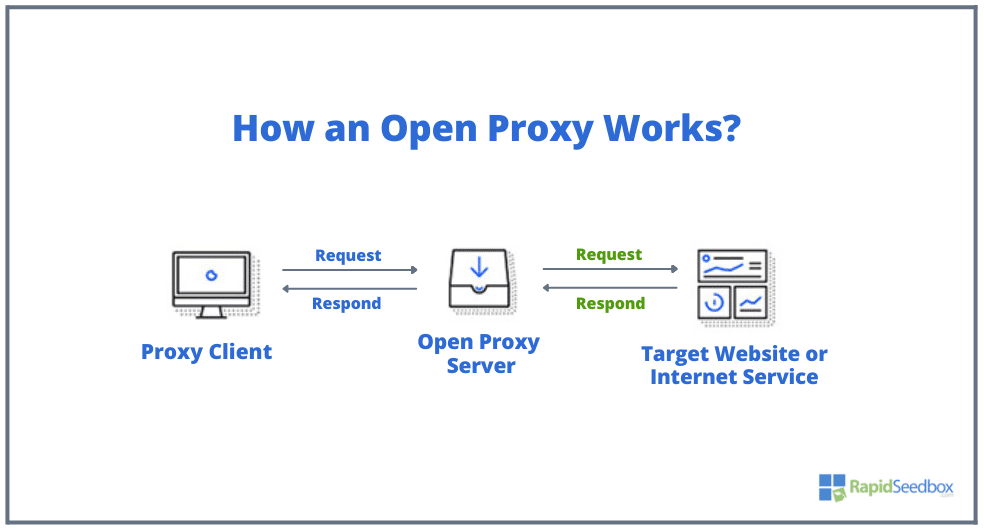
Here’s a step-by-step breakdown of the process depicted in the picture above:
- Proxy Client: This represents you or any internet user’s device. When you want to visit a website or use an online service, your device sends out a request. This request usually contains your IP address and other data that could identify you.
- Open Proxy Server: Instead of sending your request directly to the website, it first goes to an open proxy server. The key function of this server is to relay requests to internet services without revealing the original user’s IP address. As shown in the diagram, the open proxy server receives your request, performs an action (like changing IP), and then forwards it to the intended destination.
- Target Website or Internet Service: This is the final destination for your request, whether it’s a website, online platform, or any other Internet service. Due to the intervention of the open proxy, the target website perceives the incoming request as originating from the proxy server, not from your personal device.
- Response Path: Once the target website processes the request, it sends the required data or response back to the open proxy server. The server then forwards this response to you, the proxy client. Throughout this process, your identity and location remain hidden from the target website.
2. Comparison Table: Pros and Cons of Open Proxies
| Pros | Cons |
| Enhances online anonymity by hiding the user’s IP address | Potential security risks, as they can be exploited by cybercriminals |
| Allows access to regionally blocked content and services | Lack of strong security measures, leading to possible data breaches |
| Generally free and easy to use | May slow down internet speed due to server congestion |
| Useful for bypassing internet censorship | Lack of privacy, as open proxies might monitor and log user activity |
| Legal and ethical concerns, particularly if used to bypass content restrictions or licensing |
Verdict:
Open proxies are perfect for keeping your online identity protected and getting around those annoying location blocks on websites and videos. Plus, they’re usually free and quite easy to set up. But, and it’s a big but, they’re not exactly Fort Knox when it comes to security. There’s a chance some sketchy proxy providers could use the inviting “open proxy” to snoop on your internet activities. Plus, open means anyone can come in, which also means slower speeds, and if you’re using them to sneak into services or content you shouldn’t, that’s kind of walking a fine line, legally speaking. So, open proxies? They’re handy, but just be conscious about how you use them.
Want a safe, trustworthy, and untraceable proxy?
Check out Rapidseedbox’s closed proxies. Enjoy high-success rate IPv4 and IPv6 proxies optimized for daily use. Build your secure proxy server list with our advanced and user-friendly proxy services.
3. Open Proxies: Use Cases.
People use open proxies for a few reasons, like getting around online restrictions, keeping their activities private, and for testing. But while these perks are nice, it’s important to remember that using open proxies can be risky.
Here are some of the things people use open proxies for:
- Bypassing Geo-Restrictions: Open proxies are useful for accessing content that is restricted in certain countries. They help route traffic through a proxy in a region where the content is available.
- Maintaining Anonymity: Another popular use case for these types of servers is for hiding one’s IP address to browse the internet without revealing identity. This is particularly valuable for whistleblowers or journalists.
- Circumventing Censorship: Open proxies can also be used to overcome government-imposed internet restrictions. The idea of free and open internet access is possible with an open proxy.
- Research and Data Collection: Marketers and data analysts can use open proxies to easily collect intel without being caught. This is important for keeping tabs on the competition and coming up with solid SEO strategies.
- Testing Websites: Web developers can use open proxies to view their websites from different locations and ensure they are properly localized and working as expected.
- Avoiding Bans and Blacklists: Users who have been banned or blacklisted from certain services can regain access by connecting from a different proxy server. A proxy is like having a secret tunnel to bypass the ban and regain access. Learn more about this: Your IP has been banned.
- Security Testing: Ethical hackers and cybersecurity pros also use open proxies to check out how secure a network really is. They use these proxies for testing their network from different places around the world.
Worldwide access with open proxies.
One of the most popular and useful use cases of an open proxy is to bypass geo-restrictions. Users can route their traffic through proxy servers in different countries. This allows them to access content and services without restrictions. For example, if a website is blocked in a user’s country, they can access it through an open proxy in a country where it’s available.
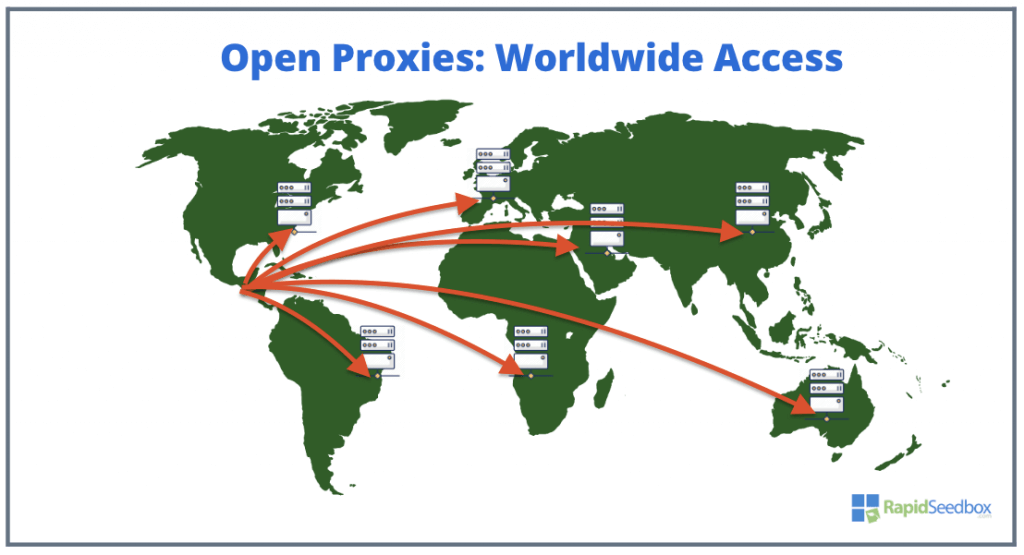
The previous picture shows a map with server icons representing a global network of proxy servers available for users to:
- Circumvent geo-restrictions and censorship.
- Anonymize their online presence.
- Access diverse content as if from varied locales.
4. Open Proxies vs Closed Proxies
Whether open or closed, any type of proxy acts as an intermediary between users and the internet, but they differ in various aspects such as accessibility, control, cost, privacy, security, and more.
On the one hand, open proxies offer a gateway to the internet with no entry barriers, promising anonymity and freedom. On the other hand, closed proxies are like private channels that cater exclusively to a select audience, emphasizing security and control.
The below diagram shows the core difference. Open proxies are publicly available with no restrictions, while closed proxies are gate-kept, serving a limited number of users, usually within a private network.
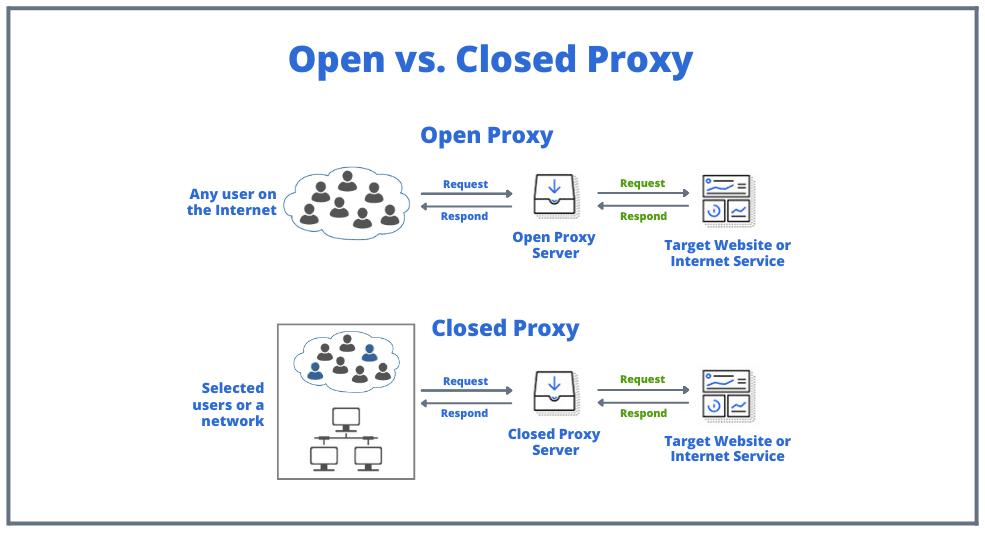
Let’s define more differences:
Open Proxy:
- Accessibility: Open to any user on the internet, with no authentication required or cost involved.
- Functionality: The open proxy server relays requests from the user to the target website or internet service, masking the user’s original IP address.
- Use Case: Ideal for users seeking anonymity and circumventing geo-restrictions. Open proxies provide a universally accessible point of relay for web requests. Plus, they are generally free and easy to use.
Closed Proxy:
- Accessibility: Restricted to selected users or devices within a specific network, often requiring credentials for access.
- Functionality: Similar to the open proxy in operations, the closed proxy server forwards user requests and returns responses from the web. However, it serves a controlled user group.
- Use Case: Typically employed within corporate or educational networks to enforce internet use policies, content filtering, and added security. These proxies can also be used for advanced applications such as web scraping, SEO proxy, marketing and more.
5. Open Proxy Lists Providers and Tools.
This section features selected open proxy providers and proxy tools. It includes detailed information about various proxy services, ranging from updated proxy lists to specialized tools for managing and employing proxies on different platforms like Windows, macOS, and web browsers. These resources are essential for effectively utilizing open proxies for diverse online needs.
Popular Open Proxy Lists Providers.
The following list presents a selection of well-known providers of open proxies and open proxies lists. Each offers unique features and tools to facilitate anonymous browsing and access to restricted content.
- ProxyNova: Offers tools like proxy server lists and checkers, focusing on anonymous browsing and accessing restricted content. It’s useful for enhancing network performance and accessing blocked websites.
- Spys.one: A Russian proxy site that provides a real-time updated database of various proxies, emphasizing anonymity. It includes tools for IP checks and proxy testing, suitable for users needing reliable proxy servers.
- Webshare.io: Known for both free and premium proxies, focusing on anonymity. Offers diverse proxy services with a technology-driven approach, ideal for beginners but with varying free proxy performance.
- Free-Proxy-List.net: Features a frequently updated list of free proxies, offering a user-friendly interface and a unique proxy API. Great for those seeking anonymous internet access.
- Proxy-List.download: Offers a wide range of updated free proxy servers, testing each for quality and reliability. Includes a Proxy API and Scraper tool, catering to secure and anonymous internet access needs.
- Proxy-List.org: A well-established provider of free proxies, offering a variety of options with different anonymity levels. Allows users to search for proxies by type and download lists in various formats.
Useful Proxy Tools
This section provides you with a rundown of different proxy tools and what they can do. From full-on proxy managers to testers, clients, and even add-ons, there’s something for everyone. They work on Windows, macOS, and even in your browser, helping you test, manage, and use open proxies like a pro.
- ProxyCap: Useful for selectively routing internet traffic through open proxies based on user-defined rules. ProxyCap performs selective routing for Windows and macOS.
- WinGate: Ideal for managing open proxies on a network, enhancing security, and controlling access. Check out our complete WinGate review.
- Proxifier: An advanced proxy client. It is efficient for directing specific applications to use open proxies, even if they don’t support proxy settings natively. If you are interested, learn more about Proxifier.
- Proximac: An open-source advanced proxy client for macOS. It allows its users to route their applications’ traffic through open proxies.
- Elite Proxy Switcher: A professional proxy software. It is handy for testing the functionality of open proxies and integrating them with browser settings.
- IPRoyal Browser Extensions: Facilitates easy switching and management of open proxies directly from the browser.
- FoxyProxy Basic: A Mozilla addon that simplifies the use of open proxies in web browsers with easy configuration and switching.
- XX-Net: A proxy tool designed to bypass the GFW. It is useful for bypassing internet censorship and restrictions using open proxies.
- Tinyproxy: A lightweight HTTP and HTTPS proxy daemon. It is effective for setting up a fast and lightweight open proxy server for HTTP and HTTPS.
- Mitmproxy: Ideal for intercepting, inspecting, modifying, and replaying web traffic using open proxies.
- WhatIsMyIP: Provides IP lookup services to verify the efficacy of open proxies.
- WhatIsMyIP Proxy & TOR Node Check: Useful for verifying if an IP is from an open proxy or a TOR node.
6. FAQ On Open Proxies.
a. Why would we recommend an open proxy?
Open proxies enhance online privacy and bypass regional content restrictions. They are useful for accessing services or websites blocked in a user’s location, and they help maintain anonymity while browsing the internet.`
b. Why would we not recommend an open proxy?
Open proxies are not recommended due to security risks. They can be targeted by cybercriminals and may inadvertently facilitate access to harmful or malicious content. Open proxies also lack robust security measures, making them vulnerable to data breaches and privacy violations.
c. What are some of the top and most popular Proxy list providers?
Proxy-list.org, freeproxylists.net, free-proxy-list.net, Proxyium.com, and proxy-list.download, and webshare.io. These sites are popular for providing open proxy lists and some of them have been around for a long time. As with any open proxy, you should always be aware of the risk and security implications when using free and open proxy services.
d. Why is my IP flagged as an open proxy?
Your IP might be flagged as an open proxy if it has been detected allowing anonymous connections from different users. This possibly indicates your IP is part of a proxy network. This can happen if your IP is being used without your knowledge as a proxy or if you’re intentionally running a proxy service. If you are unaware, run anti-malware or anti-virus software and uninstall any suspicious programs that were lately installed.
e. How do you detect an open proxy? How do you know if your IP is an open proxy?
Detection of open proxies typically involves testing IPs for proxy behavior, like accepting connections from external addresses and forwarding requests. If your IP allows such behavior and is accessible to anyone online, it might be identified as an open proxy.
f. How to disable open proxies?
To disable open proxies, you need to secure your network. Start by configuring your router and firewall settings to restrict unauthorized inbound connections. Additionally, regularly update your security protocols and check for any unintended proxy services running on your network.
g. How do you find open proxy servers?
Finding open proxy servers usually involves using specialized websites and services that list IPs functioning as open proxies. These sites often categorize proxies based on type, speed, country, and level of anonymity. Refer to the previous section “Popular open proxy providers” to find open proxy servers.
h. What legal and ethical considerations should be taken into account when using open proxies?
When using open proxies, it’s important to consider legality and ethics. Respect the privacy and security policies of websites you access, and be aware that some proxies might be used for illicit activities, which could implicate users. Always ensure your actions comply with both local and international laws.
i. How can open proxies affect internet speed and reliability?
Open proxies can impact internet speed and reliability due to the additional data routing and potential heavy traffic from multiple users. The quality and speed of the proxy server play a significant role in determining the overall browsing experience.
j. What security measures should be in place when using open proxies?
When using open proxies, implement strong security measures like using VPNs for encryption, avoiding sensitive transactions, and keeping antivirus software updated. Be cautious about the data you transmit over open proxies, as they might not be secure.
7. Final Words.
While open proxies are handy tools for privacy and overcoming content barriers, users must navigate their security risks wisely. It’s essential to balance their benefits against potential vulnerabilities.
Open proxies can be super useful for keeping your privacy on the down-low and getting around those nasty content blocks. But, here’s the catch – you have to be on the lookout and be smart about the security risks that come with them.
It’s all about weighing the pros and cons!
0Comments